Why Data-Driven Human Risk Management
Beats Intuition

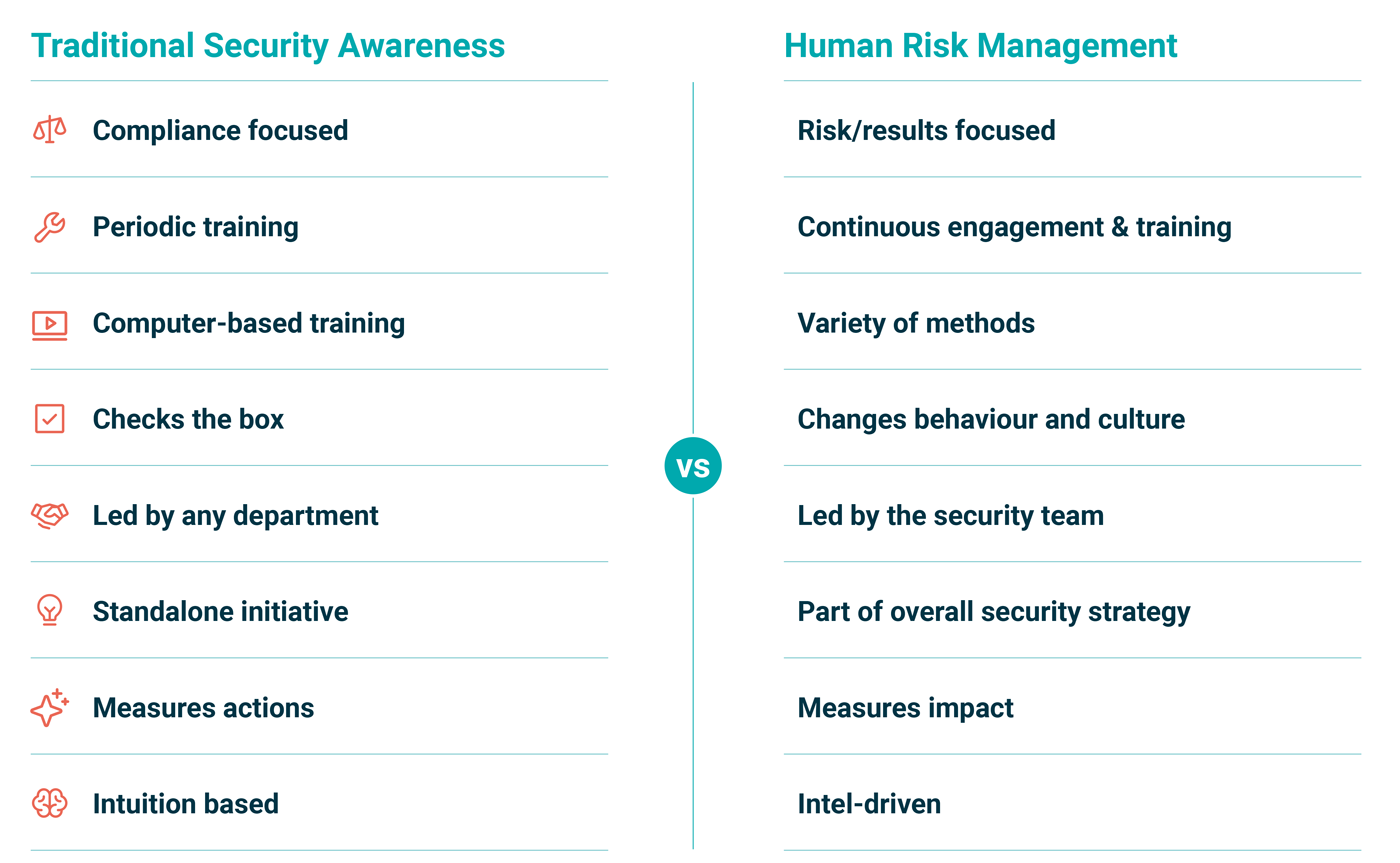
The Problem With Traditional Cyber Safety Initiatives
For years, organisations have approached cyber security awareness with a checklist mentality. When it comes time to “do something about human behaviour risks” the go-to solutions are generic e-learning modules, phishing simulations, and campaigns to warn about new cyber threats. At face value, these initiatives look like a proactive approach to security but, in reality, they rarely catalyse meaningful change. Why?
Traditional security awareness programs have significant limitations that prevent them from truly mitigating human risks. Here are some common “red flags” that indicate your efforts are probably ineffective:
- Everyone in the office completes the same e-learning programme, regardless of their role, risk exposure, or knowledge.
- Security training doesn’t account for the organisation’s specific threat landscape, existing technical controls, or maturity level.
- Employees receive training that contradicts or ignores existing company policies.
- Policies are vague or very difficult and time-consuming to follow.

The Case For Human Risk Management
As with any change, shifting from a traditional awareness models to Human Risk Management will likely first take some convincing within the organisation. Leadership buy-in is imperative. It’s important for the executive board to understand that, without measurement, organisations risk wasting both time and resources on training that is misaligned with actual behaviours. Here are some other challenges to promoting cyber safe behaviour that can be addressed with scientifically-validated initiatives.
People Have Limited Attention
Employees juggle many different tasks daily, and cyber security is just one of them. If training doesn’t feel relevant, it’s quickly forgotten or ignored. Organisations must prioritise the most important risks for each team rather than overwhelming and burdening employees with content that doesn’t apply to their roles.
For example, an IT team is already well-versed in spotting phishing attempts. Requiring them to complete phishing training wastes time and offers little value. Instead, their focus should be on risks like improper data sharing or credential management—areas where even small mistakes can have significant consequences.
By pinpointing where security attention is most needed, organisations can implement training programs that are focused and beneficial. The goal is to spend time and resources on factors that will make the most difference. This also means using employees’ time and attention wisely. Some cyber behaviour risks can actually be mitigated with technology solutions. So, let’s not ask people to do all the heavy lifting if we can solve the problem with technology.
Intuition Is Often Wrong
A common assumption is that employees resist security training. Many security leaders view training as an uphill battle because employees don’t care or see it as an inconvenience. And yet, data tells a different story.
After assessing cyber safe behaviour and predictors of more than 9000 workers across diverse companies, we have consistently found that most employees are willing to learn about security. This is especially the case when the training is engaging, relevant, and framed in a way that helps them in their daily work.

Unfortunately, when organisations base cyber safety strategies on pure intuition, security teams often end up on the wrong problems instead of addressing areas where employees actually need support. The good news is that these efforts don’t have to be in vain. After all, the real issue isn’t resistance–it’s poorly designed training that doesn’t feel useful.
Every Organisation is Different
Cyber risks are not one-size-fits-all. The challenges faced by a global financial institution will differ from those of a tech startup or a healthcare provider. Even within the same industry, companies have unique risk profiles based on:
- Size and structure (e.g., a small company with no dedicated security team vs. an enterprise with a mature SOC)
- Existing security measures (e.g., automated defences reducing certain human risks)
- Industry-specific threats (e.g., social engineering attacks in finance vs. ransomware risks in healthcare)
By measuring human risk at an organisational level, companies can tailor interventions to the specific challenges they face. This way, security training is not just another checkbox–it’s a strategic tool to address real-world threats.
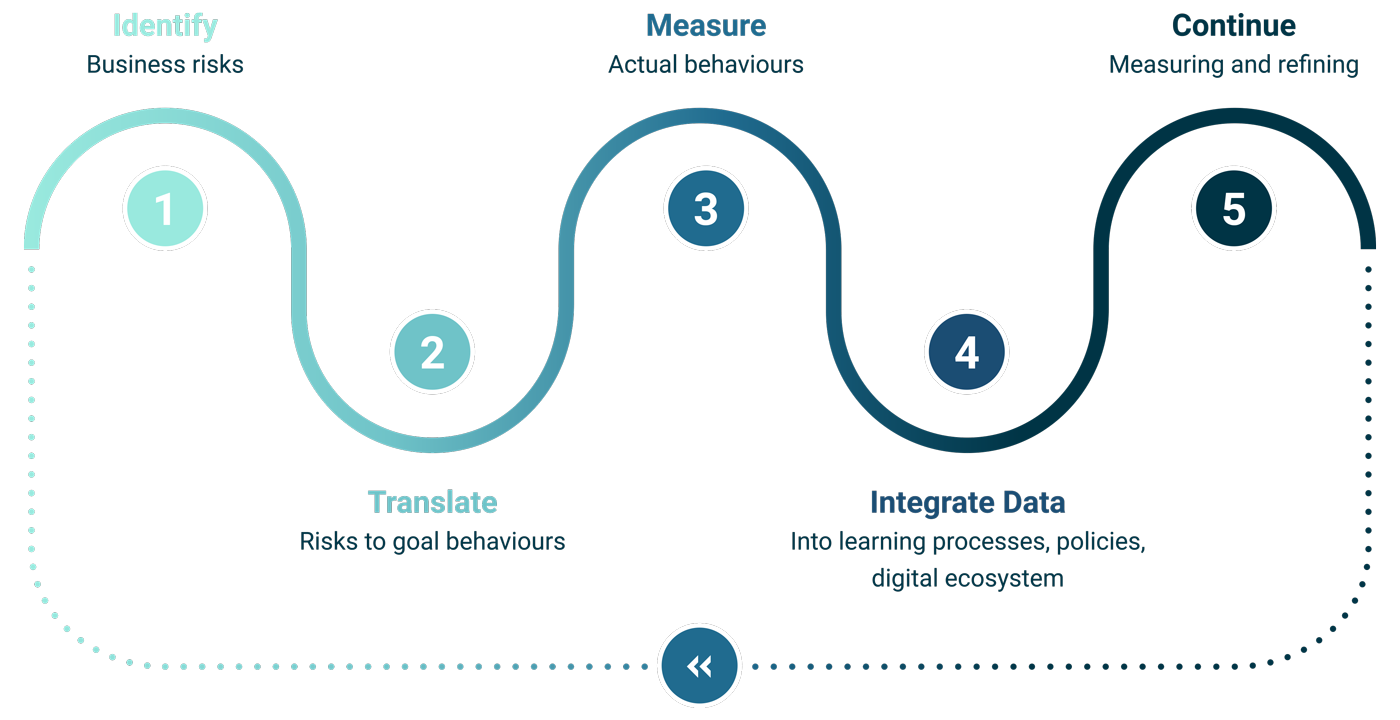
How to Apply Scientific Measurement to Human Risk Management
Now that you’ve challenged some common assumptions about managing human behavioural risks, the next step is to start collecting and analysing your data. Assess real behaviours in the workforce, knowledge gaps, and organisational influences.

Actual Human Behaviours
Instead of relying on intuition, organisations should track how employees interact with data, passwords, and third-party tools. Measuring actual behaviours provides a realistic picture of security risks and allows teams to prioritise interventions where they are needed most.
For example, many security teams don’t think they need to explain password management tools to employees. And yet, when we surveyed employees in companies that have implemented a password management tool, a significant portion (42%) of respondents said they don’t know how the tools work. In that case, a little more explanation can make a big difference.

Key ways to gather cyber behaviour data include:
- Technical logs – Monitoring access patterns, file-sharing activity, and authentication methods to identify risky behaviours.
- Incident reports – Analysing past security events to detect recurring human errors.
- Security tool data – Reviewing metrics from phishing simulations, endpoint monitoring, and authentication systems to gauge employee responses to threats.
- Survey Employees – Simply ask how people are using digital tools in the workplace. An anonymous survey could ensure a more accurate picture.
Knowledge Gaps
A critical component of measuring human risks is identifying where employees lack security knowledge and how that impacts behaviour. Knowing a risk exists isn’t enough. Organisations must understand why employees are struggling and where their knowledge gaps are.
One major issue is policy awareness. Employees can’t follow security policies if they don’t know where to find them, don’t understand them, or if they’re not communicated at all. Lengthy written policies that aren’t actionable may also be a deterrent. A simple knowledge assessment or anonymous survey can reveal whether employees:
- Know the organisation’s security policies
- Understand the reasoning behind security controls
- Recognise risky cyber behaviours
- Are able to report incidents or security concerns
- Can use the organisation’s security tools, such as password managers and data classification tools
For example, if employees are repeatedly clicking on phishing links, it might not be a lack of caution. Instead, it could be that they don’t know how to verify a sender or the phishing detecting and reporting guidelines are unclear. Understanding this gap allows organisations to tailor security training and protocols accordingly.

Cultural and Organisational Factors
Behavioural risks in cyber security are often a symptom of organisational culture and leadership dynamics. If policies aren’t reinforced by managers or embedded in daily workflows, employees are less likely to prioritise them.
For instance, if employees regularly reuse passwords, the real culprit might be overly complex password requirements. Similarly, if employees are not reporting security incidents, they might fear negative consequences or even feel it’s not worth the effort. It’s important to understand that you don’t gather data on cyber behaviour to penalise employees. The aim is to examine the broader factors and use the insights to address root causes of risky behaviours.
Here are ways to start assessing your cyber security culture:
- Managerial reinforcement – Do team leaders actively support security initiatives?
- Policy clarity – Are expectations clearly defined, or do employees receive conflicting messages?
- Workplace pressure – Are employees bypassing protocols due to time constraints or productivity demands?

Turning Measurement into Action
The next step for organisations is to integrate behavioural data, security tool insights, and employee feedback into a continuous learning process. Adjust company security policies and the digital ecosystem to mitigate real risks to business assets. Define KPIs for different behaviours to track your organisation’s progress. And, keep measuring what matters–refining your approach based on new data, organisational needs, and changes in the threat landscape.
While this requires more effort and attention up front, the end result is that employees become active participants in security, rather than passive recipients of training. With this buy-in for cyber safety across the organisation, you can reduce risks and foster a more resilient security culture.
How Northwave Can Help
While Human Risk Management might be a newer talking point in the cyber security world, the principles aren’t new to us. As a company that has been dedicated to cyber security for 18 years, Northwave has fine-tuned a holistic approach to mitigating human cyber risks. Our programs are rooted in our real-world experiences responding to cyber incidents worldwide on a daily basis.
Northwave clients save time and security resources with our scientifically-validated Human Risk Assessments. Then, we tailor our cyber safety trainings and services to real business risks. Together, we identify specific target behaviours for the coming year, providing concrete substance to the interventions in the Human Risk Management program.
Ready to get started? Get in touch with us today to experience the difference in our risk-based, intel-driven approach.
This article is based on a presentation by Gerine Lodder, PhD, Product Manager Awareness & Human Behaviour, Northwave, during WICCON 2024. You can see a recording of the conference presentation on YouTube.
We are here for you
