Cryptojacking: is your CPU power the new gold?
Publishing date: 25th of March 2024 - By Matthijs Vos and Sander van der Maden

Recently, the Northwave Computer Emergency Response Team (CERT) responded to an incident at a professional service provider that had discovered a network intrusion. Initially, the intentions of the attackers were unclear. As our investigation showed, the central processing units (CPU) resources of our client were (about to be) misused massively for cryptomining purposes. Cryptojacking is a type of cyberattack that illicitly uses a victim’s computing power to mine cryptocurrency. It is not new, nor is it about to take over ransomware as the cybercriminal’s favourite business model. But it is increasing, and the financial damage to an organisation can be significant.
In this article, you will learn more about the attack, the potential impact of cryptojacking, and what can be done about it.
The incident: an unknown intruder
Our CERT-team was called to action by a medium sized business service provider with a considerably large IT infrastructure on premise. They were alarmed by an inexplicable multi-factor authentication (MFA) request for an administrator account. After some investigations by the client, they found remote access tools that were installed on multiple hosts within their network, but not by themselves. So far, it was not clear what the purpose of this intrusion was.
Northwave was asked to find out how the attackers gained access and created persistency, and whether they still had access. The underlying question was: what were the intentions of the threat actor(s)? In addition, Northwave was tasked with assisting in recovering the IT environment in a secure manner.
The investigation: keeping all options open
Our investigation became an interesting combination of forensics and threat hunting. We categorised our findings into three separate attack phases:
- In - How did the attackers gain access to the network?
- Through - How did the attackers move through the network?
- Out - How did they use the network access to monetize the attack?
Let’s take a closer look at what we discovered per phase:
IN |
|
Initial access The threat actors gained initial access by logging on to a terminal server using Remote Desktop Protocol (RDP). To do so, they used valid credentials and were able to bypass multi-factor authentication (MFA). Due to limited retention of the authentication logs, it was not possible to determine how the threat actors were able to authenticate. Persistency After bypassing MFA for almost two weeks, they created persistency by using legitimate remote access tools to consolidate their remote access |
THROUGH |
|
Discovery and lateral movement Different legitimate (pen testing) tools were used to explore the internal IT domain of the client and to acquire additional credentials.2 Privilege escalation Establishing their foothold, the threat actors escalated their privileges to domain accounts (by retrieving valid domain administrator passwords from several domain controllers) and used previously acquired credentials to create local accounts. |
OUT |
|
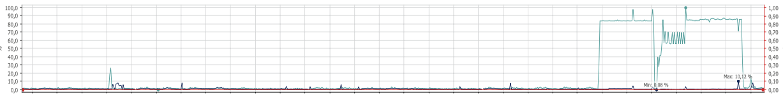
(Generic) data collection Some servers showed evidence of data collection of generic files like password stores and browser profiles. Data that was relevant to following through on the attackers’ objectives. This was archived in ZIP files, probably for exfiltration purposes. No traces of collecting or exfiltrating sensitive corporate data like financial information, annual reports, or employee and customer data were found. Coinminer deployment After being inside the network for at least 17 days, the threat actors started to propagate and deploy a coinminer called XMRig to be able to mine the Monero (XMR) altcoin. A PowerShell script was crafted to deploy the coinminer script on multiple hosts. The threat actors used scheduled tasks to start the coinminer executables. The miner was deployed to at least 1600 server systems within the IT domain of our client. We observed at least a few of these hosts connecting to the port of a mining pool. Crypto miners use a mining pool to share processing (CPU) power to split the reward equally, according to the amount of work they contribute. The connection to the mining pool indicated that the miners were indeed active. Moreover, the hosts concerned showed an unusual high CPU usage (see figure 1).
Figure 1: CPU usage of one of the hosts that had an active miner installed.
|
The table below provides a closer look at the tactics, techniques and procedures (TTPs) per phase of the attack, referring to the MITRE ATT&CK framework.
| Technique title | ID | Tactic | Tools or protocols used |
| Initial Access - IN | |||
| External Remote Services | T1133 | Initial access | Remote Desktop Protocol (RDP) |
| Initial access | |||
| Local account creation | T1136.001 | Persistence | |
| Scheduled Task/Job | T1053 | Persistence | |
| Valid account login | T1078 | Defence evasion | |
| Remote access software | T1219 | Command and Control | Atera, Splashtop, AnyDesk |
| Ingress tool transfer | T1105 | Command and Control | sysdaemon.exe, PowerShell |
| Lateral Movement - THROUGH | |||
| Network Service Discovery | T1046 | Discovery | Advanced IP Scanner |
| Account discovery | T1087 | Discovery | AD Explorer, PowerShell, PingCastle |
| Browser information discovery | T1217 | Discovery | |
| Domain controller listing | T1087.002 | Discovery | PowerShell |
| Valid domain accounts | T1078.002 | Privilege escalation | |
| Credential dumping | T1003 | Credential access | crackmapexec |
| Action on Objectives - OUT | |||
| Archive collected data | T1560 | Collection | |
| Resource hijacking | T1496 | Impact | XMRig cryptocurrency miner |
The TTPs used in the IN and the THROUGH phases of the attack may have been indicative for the build-up of a ransomware attack. The way the attackers created persistency and escalated their user privileges is something we typically observe during ransomware investigations. On the other hand, there were no indications of the collection and exfiltration of (large amounts of) company-sensitive data. Exfiltration of this type of data would have been common for a ransomware attack. Nor did we find evidence of ransomware being delivered and installed. The discovery of the sysdaemon.exe binary led us towards the cryptojacking attack. This binary was used to download the XMRig cryptocurrency miner. Also, the PowerShell script found for deploying the miner was specifically intended for this deployment. Finally, we observed some of the miners already actively connecting to a mining pool and eating CPU power. This was the final piece of evidence that confirmed the attackers’ motive.
Why worry about cryptojacking?
As the attack showed, in the case of cryptojacking an attacker illicitly uses the victim’s (cloud) computing resources to mine cryptocurrencies to get the rewards without having to pay the computing fees. Cryptojacking requires the attacker to gain access to the victim’s infrastructure (on premise, or in the cloud) and acquire administrator rights, often by using compromised valid credentials. But, if no company-sensitive data is exfiltrated, and if systems are not being encrypted, why worry about cryptojacking?
First, because cryptojacking is on the rise, and it is moving to the cloud to increase scalability. Cryptojacking broke records in 2023 with more attempts recorded that year than in the entire period between 2018 and the end of 2022[1]. And from our own observation, cryptojackers will misuse anything they can to create the desired computing power: from CPU’s to graphics processing units (GPU’s), to data processing pipelines, to caching tools, to spinning up their own virtual machines in your IT domain.
But cryptomining is only financially viable when it is done on a significant scale. And because not every network is as large as that of our client in this case, cybercriminals are shifting from infecting end-user machines to targeting cloud services. Recently, we investigated a case where a cryptojacker was spinning up a large number of virtual machines within the Azure subscription of a victim.
Second, because it will drain your CPU or GPU power. This may disrupt your business continuity. Above all, it will cost you money. The abuse of (cloud) computing resources causes financial loss to targeted organisations due to the increase of computing fees. An analysis in 2022 of TeamTNT, a cloud-targeting threat actor specialized in cryptojacking, revealed that for every $1 of Monero (XMR) mining profit by this group, its victims were billed $53[2]. Cryptojackers prefer to mine Monero, which offers the highest CPU mining returns among cryptocurrencies and is harder to trace on the blockchain. More recently, Microsoft observed targeted organisations losing more than 300.000 euro in computing fees due to cryptojacking attacks[3]. We even have encountered losses of up to 550.000 euro when responding to cryptojacking cases.
Finally, the fact that your network is being abused for cryptojacking means that an attacker has access to it. When mining cryptocurrencies isn’t viable anymore, the attacker (or other cybercriminals) can choose to change tactics and exploit your network and your data in other ways like ransomware or data theft.
What to do against it?
As is the case with all threats, the risk of cryptojacking attacks can be managed. Below we highlight some controls that once in place, will help to reduce both likelihood and impact.
- Fully implement and control baseline measures like multifactor authentication across all accounts, vulnerability management, update-management, network segmentation and cloud hardening. Keep these measures up to date.
- Assess the risk of cryptojacking for your organisation. Although cryptojacking attacks do not appear to be very targeted, networks with extensive computing resources or with unused Azure subscriptions may be more attractive to cryptojackers.
- Implement Endpoint Detection and Response (EDR) as a tool for identifying anomalous behaviour and breaches.
- Implement health monitoring of CPU usage, as well as cloud cost monitoring (including virtual machines and hypervisors). This would enable you to detect largescale, unusual high CPU usage in a timely manner. Be sure that the rules for these types of monitoring are being monitored themselves as well, so that no threat actor can alter them unnoticed.
- Manage and monitor core quota: Manage the ability for users to increase core quota in your Azure tenant and monitor for suspicious increases as well.
- Monitor and/or block network connections to mining pools. Connections to any mining pool should sound the alarm. Below, we have added a (not exhaustive) list of currently known pools that are frequently used by cryptojackers as indicators of compromise (IOC’s).
- Secure and separate domain administrator accounts. Not only should (global) domain administrator accounts be separated from normal user accounts. On-premise domain administrator accounts should be kept apart from cloud domain administrator accounts as well. Use multi factor authentication and conditional access management where possible and monitor access elevation. Make sure that local domain administrator accounts are not synced to Entra ID, and that Entra ID privileged accounts are cloud-only accounts. This will make it harder for an attacker to hop from your on-premise environment to your cloud domain.
- Create forensic readiness within your IT domain. This entails policy regarding the availability and analysability of data that is relevant for incident response and forensic investigation. For example, retain available network flow logs, deep visibility logs or MFA logs for an adequate period of time.
Conclusion
As our investigations shows, it is always worthwhile keeping different scenarios and hypotheses open when responding to an incident. Cybercriminals will keep looking for (new) ways to monetize entrance to any network.
Although there are indications that cryptojacking is increasing, we assess that from the criminal’s perspective, it is still much less profitable than cybercriminal extortion tactics like ransomware and data leaks. Also, the profitability of cryptojacking depends very much on the Bitcoin and altcoin exchange rates, which are very volatile. But then again: cryptojacking can have a significant financial impact on your organisation, while feeding the wallets of the cryptojackers.
[1] https://blog.sonicwall.com/en-us/2023/08/cryptojacking-continues-crushing-records/
[2] https://sysdig.com/press-releases/sysdig-threat-report-reveals-victims-lose-53-for-every-1-cryptojackers-gain/
[3] https://microsoft.com/en-us/security/blog/2023/07/25/cryptojacking-understanding-and-defending-against-cloud-compute-resource-abuse/
We are here for you
Need help with getting your organisation ready for DORA or wondering far along you your business currently is?
Get in touch and we will guide you with your next steps.