Inside The World Of Ransomware-part 3/3: CONTI, RYUK and HIVE affiliates, the hidden link
On the 5th of August 2021, a ransomware affiliate of the Conti ransomware gang leaked training material of the cyber-criminal organization [1]. The training material contained numerous tools and a playbook, written in Russian, for carrying out a ransomware attack.
On the 2nd of September 2021, Talos released a version of the playbook translated to English [2]. Upon reading the Conti playbook, Northwave found that large parts of the playbook matched the modus operandi of a ransomware affiliate group that Northwave has been tracking since early 2021. Northwave considers it very likely that this affiliate has operated for the Ryuk and Hive ransomware gangs. Furthermore, based on an investigation done by TheDFIRReport [3] , we believe the affiliate also works for the Conti ransomware gang. Since the modus operandi of this affiliate pre-dates the origins of the Conti ransomware gang and matches very closely with the training materials provided by Conti, it might be possible that this affiliate was involved in developing the training program and training new criminals to attack companies. During the investigation performed by Northwave CERT into the Conti chat leaks in February 2022 [4], we also found a trace of an actor claiming to be the author of a script included in the Conti playbook and observed in several attacks.
In this blog we will elaborate on the current ransomware landscape and specifically on actors fulfilling the ransomware affiliate role. We will demonstrate why we believe that a single ransomware attack involves several different actors, which all work together in a very fluid manner, where collaborations between these actors change over time. From this, we show why we believe that we have identified a common actor fulfilling the ransomware affiliate role in attacks in cooperation with several different ransomware developers.
Common Denominators Between An Affiliate Group And The Conti Playbook
In three ransomware attacks predating the Conti playbook leak, we found that the attack phases of ransomware affiliates had a similar modus operandi. This concerned three attacks where the Conti-, Ryuk- and Hive ransomware were used. We will elaborate on the roles often being fulfilled by different actors using our IN-THROUGH-OUT framework, see Figure 1.
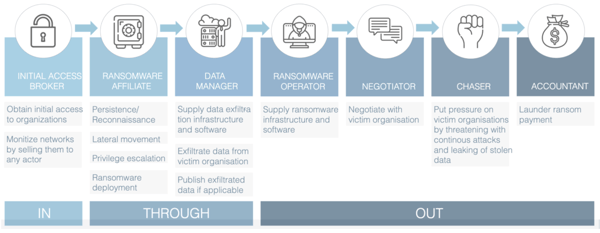
IN
In the investigations that Northwave has done where the same modus operandi for the ransomware affiliate role was encountered, the means of obtaining access to the network were different in every attack. Northwave observed that in one attack, where Ryuk ransomware was deployed, access to the network was obtained by brute-forcing a Citrix remote desktop server. In another attack where we believe the same ransomware affiliate deployed Ryuk ransomware, the means of gaining entry to the network was through phishing. A phishing mail contained a Word document with an embedded Emotet dropper. In a third attack that Northwave investigated, where we believe the same ransomware affiliate was also active, Hive ransomware was deployed. Access to the network was obtained through leaked credentials which were available on the darknet.
As we can see, the initial point of entry is different for every investigated attack. Northwave suspects that this is due to the different actors that are responsible for different roles within the ransomware attacks. We believe it to be very likely that the actor responsible for moving through a company network and deploying ransomware throughout the network (the ransomware affiliate role) is not the same actor as the one that initially compromises the network (initial access broker role). This can be seen in Figure 1. Northwave believes that actors fulfilling the ransomware affiliate role work together with more than one initial access broker. Each actor fulfilling this role likely makes use of their own methods. Examples are phishing as seen in one of the Ryuk attacks or purchasing stolen credentials as seen in the Hive attack. Thus explaining why the point of entry in every attack is different.
THROUGH
We believe that a single actor group is responsible for the THROUGH part of the attack (ransomware affiliate activity). As such we will compare the modus operandi for each of the three attacks, as well as the modus operandi described in the Conti playbook. We then show that the methods of the group fulfilling the ransomware affiliate role were very similar in each of the attacks and similar to the playbook written for Conti affiliates. In addition to our findings in forensic investigations, the found modus operandi is also very similar to a Conti attack investigated by TheDFIRReport in August of 2021 [5], further solidifying the link between actors fulfilling affiliate roles for Conti, Ryuk and Hive.
Persistence
In all three of the attacks the actors made use of Cobalt Strike to obtain persistent access to systems within the networks. Cobalt Strike is mentioned as a tool within the Conti playbook, which we will elaborate on in the privilege escalation section below. The main methods of persistence mentioned in the playbook, which are Atera and Anydesk, were not found in any of these attacks.
In addition to Cobalt Strike, Northwave has seen that actors tend to install additional backdoors. Possibly, to ensure that when one backdoor is discovered, access to the network is not lost. This also applies to the attacks we investigated. In one Ryuk attack, the actors also deployed PowerShell Empire backdoors in addition to Cobalt Strike, which is not mentioned in the Conti playbook. During the Hive attack a SystemBC backdoor was installed on several systems next to Cobalt Strike. SystemBC is also not mentioned in the Conti playbook. We did not observe a correlation between the used “back-up” backdoor and the main backdoor. We believe these differences are most likely explained by the actor group refining their methods over time, as the core methods of the actor group remained the same over time.
Reconnaissance
In one of the Ryuk attacks reconnaissance of the network was done using the tool AdFind by executing a script called “adf.bat”. This script was also used in the attack where Hive ransomware was deployed as well as in the Conti attack detailed by TheDFIRReport [6]. The contents of the file are shown in Figure 2.
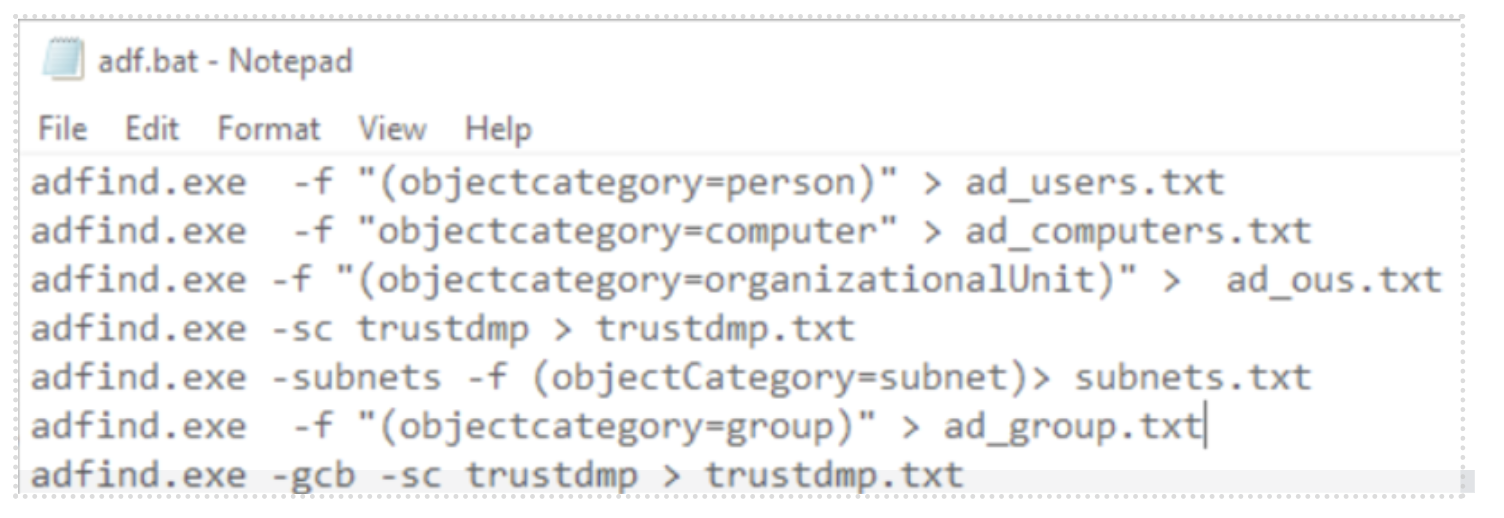
As we can see this batch file executes AdFind several times and pipes the output to several different text files. Coincidentally the “ad_users.txt” file is also mentioned within the leaked Conti playbook, as can be seen Figure 3.
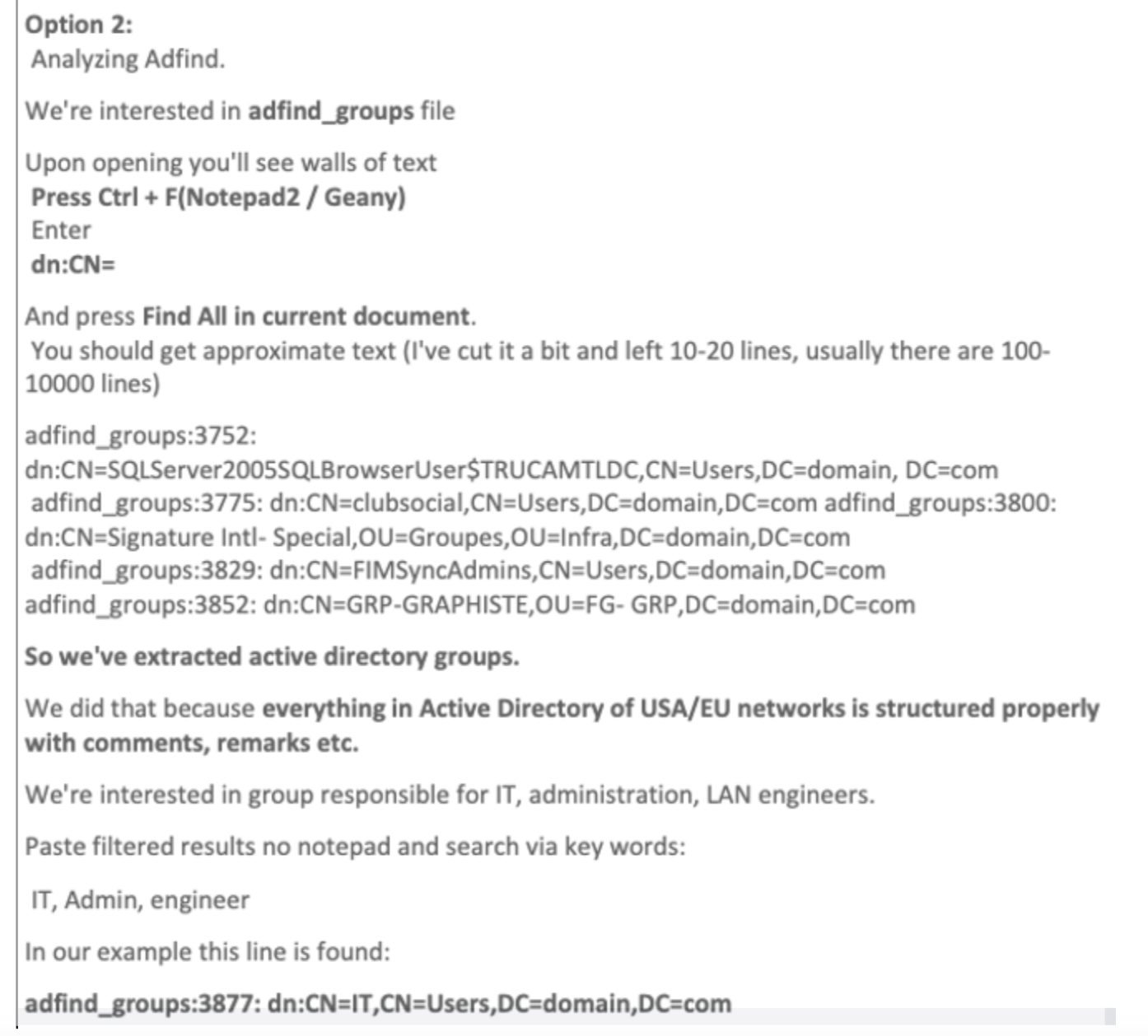
Furthermore, whilst there was no direct mention of “adf.bat” in the Conti playbook, they do recommend the use of AdFind for reconnaissance and privilege escalation, as shown Figure 3. The actor group fulfilling the ransomware affiliate role in the Conti attack reported by TheDFIRReport also made use of the same “adf.bat” to execute AdFind [7].
Northwave found that in the attacks that deployed Ryuk and Hive, the actor group used a PowerShell command to create a list of all Windows systems in the Active Directory.
Get-ADComputer -Filter {enabled - eq $true} -properties *|select Name, DNSHostName, OperatingSystem, LastLogonDate | Export-CSV C:UsersAllWindows.csv -NoTypeInformation Encoding UTF8"
This exact PowerShell command was also observed by TheDFIRReport during an attack that deployed Conti ransomware [8], which shows that although it is not in the Conti playbook, it can most likely be attributed to an actor group fulfilling the affiliate role for the Conti ransomware gang.
In all the attacks, including the one reported on by TheDFIRReport, the actors created a list of files containing all hosts present in the Active Directory, likely using the output of the aforementioned PowerShell command. These files were created on the system that would be used for ransomware deployment during the OUT phase of the attack in the folder “C:share$”. The files containing the hostnames were named in the format “comps{1-10}.txt”.
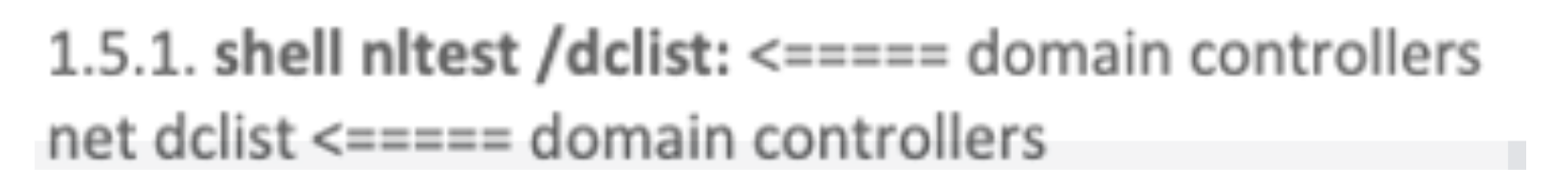
During one of the attacks, a file called DClist.txt was created, likely containing the output of the “dclist” command. Coincidentally this command is also recommended to affiliates in the Conti playbook, see Figure 4.
Privilege Escalation
There was no evidence present in the Ryuk investigations showing how the attacker obtained control of an account with Domain Administrator privileges. In the Hive ransomware case, there was some evidence showing that Mimikatz had been executed on the system, as Mimikatz output files appeared on the system. Since no Mimikatz executable had been seen executed on the system during that investigation we believe that in all three cases the affiliate used built-in functionalities of Cobalt Strike to escalate privileges. This directly matches with the Conti ransomware playbook, where they provide a step-by-step guide on how to do that (seen in Figure 5). This also matches the methodology used in the Conti attack reported on by TheDFIRReport. They mention that the actor used Cobalt Strike to elevate privileges. Furthermore, Conti actors often publish the output of the “dcsync” command (shown in Figure 5).
OUT
Ransomware Deployment
Ransomware deployment during all the attacks, with Ryuk, Hive and Conti [9] ransomware, was done through PsExec and WMI. Several batch scripts were used which were located in the “C:Share$” folder on a Domain Controller. The first file called “COPY.bat” contained code to copy ransomware to all systems on the domain using the “comps{1-10}.txt” files created during the reconnaissance phase, as can be seen below:
start PsExec.exe /accepteula @C:share$comps1.txt cmd /c COPY "\DCshare$xxx.exe"
"C:windowstemp"
The second bat file was used by the attacker, called “EXE.bat” contained code to execute the ransomware through PsExec once it had been copied, as can be seen below.
start PsExec.exe -d @C:share$comps1.txt cmd /c c:windowstempxxx.exe
The final bat file used by the attacker, called “WMI.bat”, contained the same functionality, but made use of WMI instead of PsExec, as can be seen below.
start wmic /node:@C:share$comps1.txt process call create "cmd.exe /c bitsadmin /transfer
xxx \DCshare$xxx.exe %APPDATA%xxx.exe&%APPDATA%xxx.exe"
All file names and locations were the same for all three of the attacks.
This is very similar to the modus operandi of the Conti playbook, describing the following means of deployment:
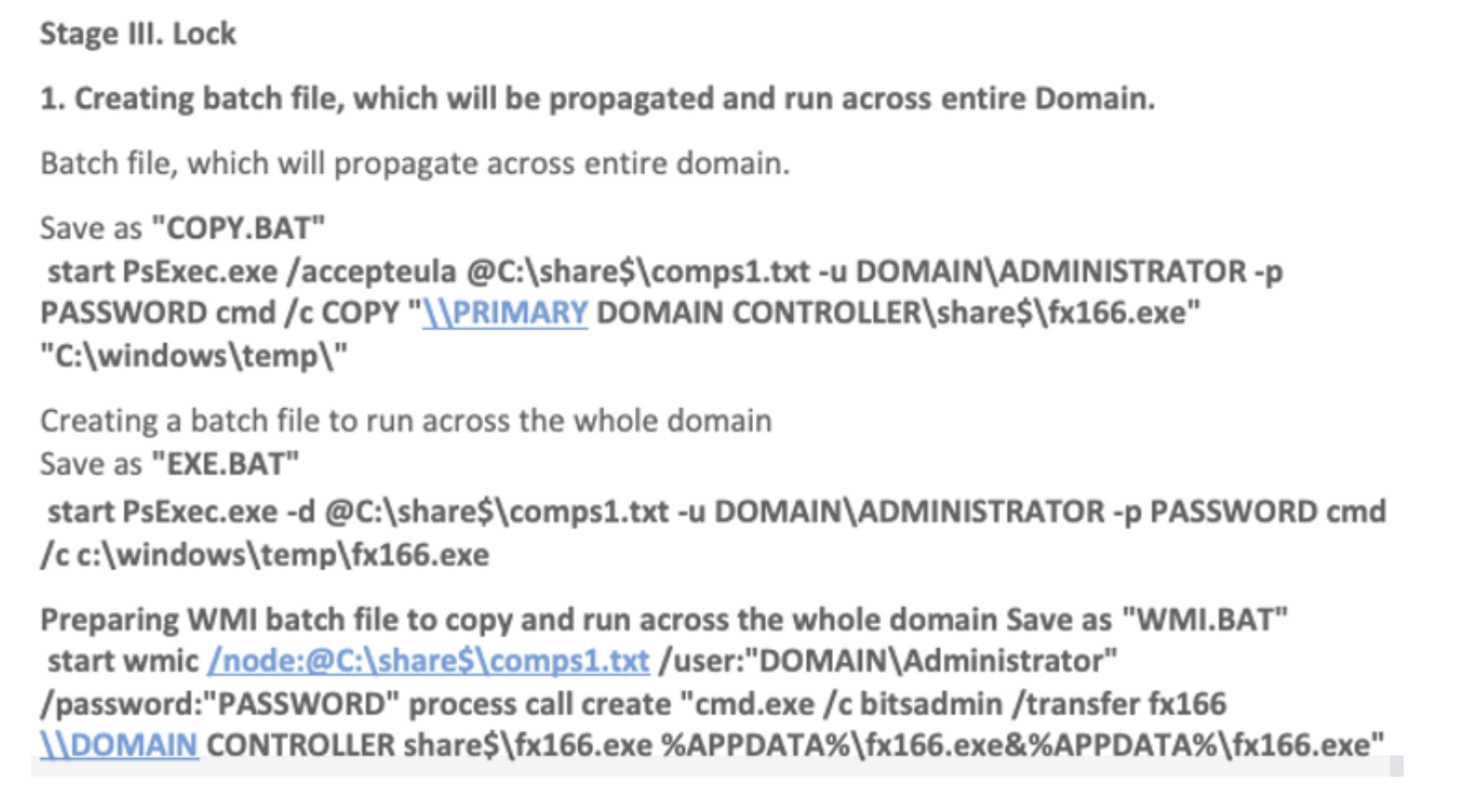
As we can see in the image above, the file names of the batch files are exactly the same as the ones used by the group of actors fulfilling the affiliate role. Furthermore, the commands found within the files are extremely similar as well. The only difference is the fact that the attacker renamed the ransomware executable to “xxx.exe” in all three of the cases that Northwave investigated and renamed the ransomware to “fQumH.exe” in the case that TheDFIRReport investigated.
Data exfiltration
No data exfiltration took place during the two Ryuk attacks that Northwave investigated. Northwave did find indications of data being collected for exfiltration during the Hive attack, however, no evidence was present indicating any method of actual exfiltration. TheDFIRReport mentioned data exfiltration being done over C2 channels in the Conti attack, which might have taken place in the Hive based attack as well.
Traces of an actor involved in the Conti playbook and with the affiliate group
The author of the adf.bat file, found in the privilege escalation phase, can be deduced from the Conti chat leaks. Northwave found that one actor, with the pseudonym “Buza” sent a link to an article written by the TheDFIRReport to another actor called “Professor”. The article discusses a write-up of a Ryuk case. In the article the adf.bat file is mentioned, to which the “Professor” responded to “Buza”: “adf.bat - finally my fucking batch file”. The full conversation is shown below:
| Date/time | From | To | Message |
| 2020-10-14 14:03 | Buza | Professor | "https://thedfirreport.com/2020/10/08/ryuks-return/ " |
| 2020-10-14 14:06 | Professor | Buza | "well, not much different from our movements" |
| 2020-10-14 14:06 | Professor | Buza | "actually almost nothing" |
| 2020-10-14 14:06 | Professor | Buza | "adf.bat - finally my fucking batch file" |
By researching the leaked chats, Northwave found that “Professor” had the role of senior developer and tester. Considering his role combined with the above messages; we find it most likely “Professor” is the author of adf.bat.
The second message reveals a fixed modus operandi exists for a group of actors fulfilling the ransomware affiliate role. Professor wrote: “not much different from our movements”, implying that a group was instructed on how to attack a network. This instruction could be the, at that time not yet leaked, Conti playbook. Given that Professor is most likely the author of adf.bat, we believe that Professor contributed to the Conti playbook.
Based on our examination of the leaked chats, we believe that the actor “Professor” was most likely involved with the group of actors fulfilling the ransomware affiliate role for the Ryuk family. We have deduced this from a conversation between the actor “Target”, believed to be a human resource manager, and the actor “Stern”, believed to be a task manager. In this conversation Target seems to inform Stern on recent collaborations with Ryuk, including the Professor, which Target seems shortens for “prof” (Northwave observed that many actors refer to the Professor as “prof” or “the prof”). Three messages on Ryuk collaborations are included in the table below:
| Date/time | From | To | Message |
| 2020-08-27 00:49 | Target | Stern | "about ryuk - next week we will start and in 1-2 weeks my people from the office will work with his people according to the scheme […]" |
| 2020-08-27 00:54 | Target | Stern | "in general, the next week - ryuk and ours will begin to learn how to interact with each other: slowly start a little - a professional on his online hackers to start earning + ran a work scheme for the office – […] - ryuk people and my senior managers themselves are already interacting - slowly start loading the office with work with prof" |
| 2020-08-27 00:58 | Target | Stern | "in October, if everything goes as the prof plans - we load the ryuk - we ship to our hackers (office) the office is you: prof: dooms: me: someone else important the prof will pull up from the backbone of the team and office employees (there will be 30-40 people in total in three offices) on salary + bonuses" |
These messages indicate that Conti and Ryuk have worked together on some level. Given that Professor was involved in this collaboration, we find it likely that the re-occurring modus operandi can be attributed to a group of actors which were instructed by Professor on attack methods.
Conclusion
Using three ransomware attacks, we have shown that in the THROUGH and OUT phase of a single ransomware attack, the performed ransomware affiliate activities can be attributed to the same group of actors.
In the IN phase, the main observation is that the initial entry point is different in all the attacks. This shows that actors fulfilling the ransomware affiliate role likely collaborate with several different actors that focus on initial access broker activities. These ransomware affiliates buy access to companies from whichever initial access broker has access to good targets at the time.
We have shown that in the THROUGH and OUT phases there is a very strong correlation between the techniques used in attacks carried out by actors using Ryuk, Hive and Conti ransomware. Since there are so many details in the ransomware affiliate activities in each of these attacks that are identical, we believe the activities are carried out by the same actors. This theory is further supported by the findings in the Conti chat leaks. This shows that it is very likely that there are actors working as affiliates that switch between ransomware families and/or follow their successors, while keeping the same modus operandi.
The fact that data exfiltration was very different in each of the attacks also shows that data exfiltration might be done by a third party or might be a requirement demanded by some of the ransomware gangs supplying affiliates with.
Sources:
[1] https://www.bleepingcomputer.com/news/security/angry-conti-ransomware-affiliate-leaks-gangs-attack-playbook/[2] https://blog.talosintelligence.com/2021/09/Conti-leak-translation.html
[3] https://thedfirreport.com/2021/08/01/bazarcall-to-conti-ransomware-via-trickbot-and-cobalt-strike/
[4] https://northwave-security.com/when-the-hackers-get-hacked-part-1-a-blog-series-unveiling-the-conti-ransomware-family/
[5] https://thedfirreport.com/2021/08/01/bazarcall-to-conti-ransomware-via-trickbot-and-cobalt-strike/
[6] https://thedfirreport.com/2021/08/01/bazarcall-to-conti-ransomware-via-trickbot-and-cobalt-strike/
[7] https://thedfirreport.com/2021/08/01/bazarcall-to-conti-ransomware-via-trickbot-and-cobalt-strike/
[8] https://thedfirreport.com/2021/08/01/bazarcall-to-conti-ransomware-via-trickbot-and-cobalt-strike/
[9] https://thedfirreport.com/2021/08/01/bazarcall-to-conti-ransomware-via-trickbot-and-cobalt-strike/
