Analysis of new active malware: MediaArena – PUA
DATE: 11 MAY 2023
intro
Over the past few days, we have observed many detections for what looks like a new type of unwanted application. All of these were classified as a variant of ‘MediaArena’ unwanted software. We found that the software was a lot more prevalent than first thought, and that having it installed poses an active security threat, so it called for a more thorough investigation. Since information about this malware is scarcely available, we are publishing this article.
Summary
‘MediaArena’ is a piece of software that masks itself as a useful tool but secretly reconfigures some browser settings to steal your search queries. It masks for instance a docx-to-pdf converter, a tool to convert video to animated GIF and so on. Distribution appears to occur via advertisements shown on webpages in an ongoing malvertising campaign. The victim is tricked to click the advert and may install this tool on their workstation. All search queries the victim enters are redirected to a third party where search results are served with ads, and the search queries are collected and sold. This allows bad actors to manipulate search, gather data on your company, inject drive-by downloads in a targeted way and do many other things. At the end of this article, you can find steps to remove the malware from your systems.
Initial findings related to MediaArena
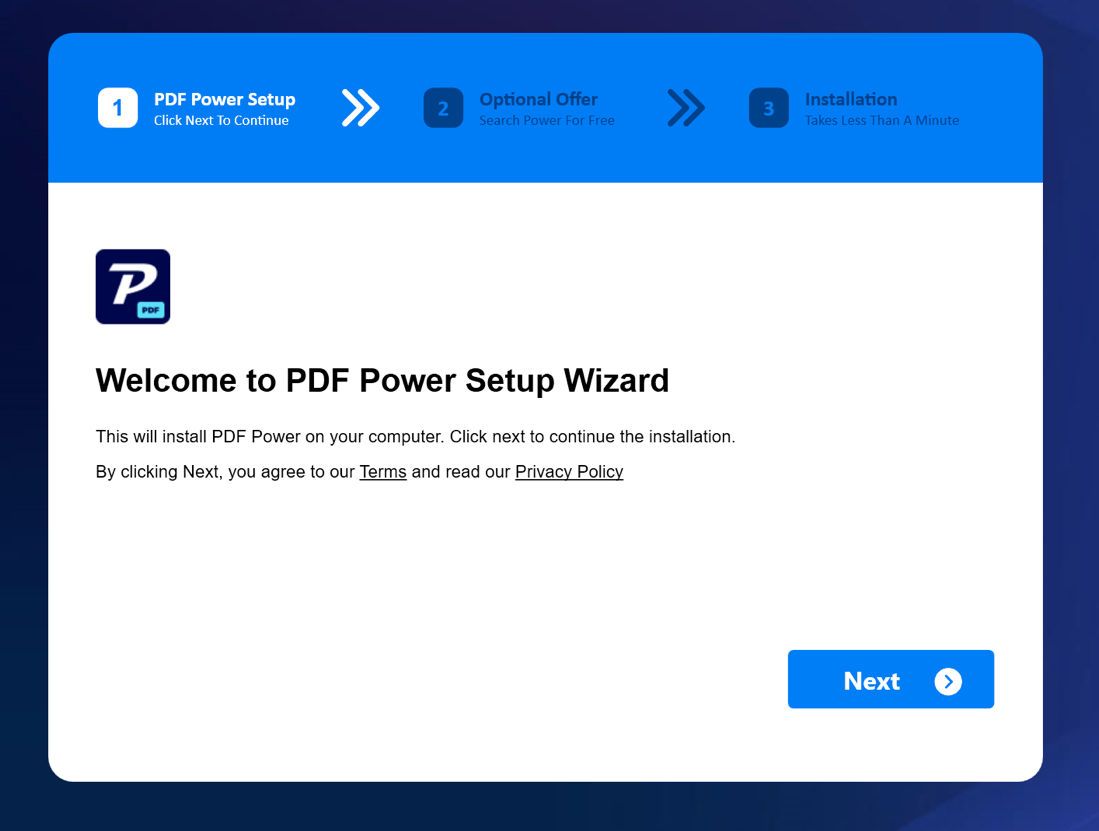
The first detection we looked at was related to a file called “PdfPower.exe”. It was detected by Microsoft Defender as “PUA:Win32/MediaArena”. The hash of the file was already known by VirusTotal [1], where it was flagged by 40 out of 70 tools. A potentially unwanted application (PUA) confirmed.
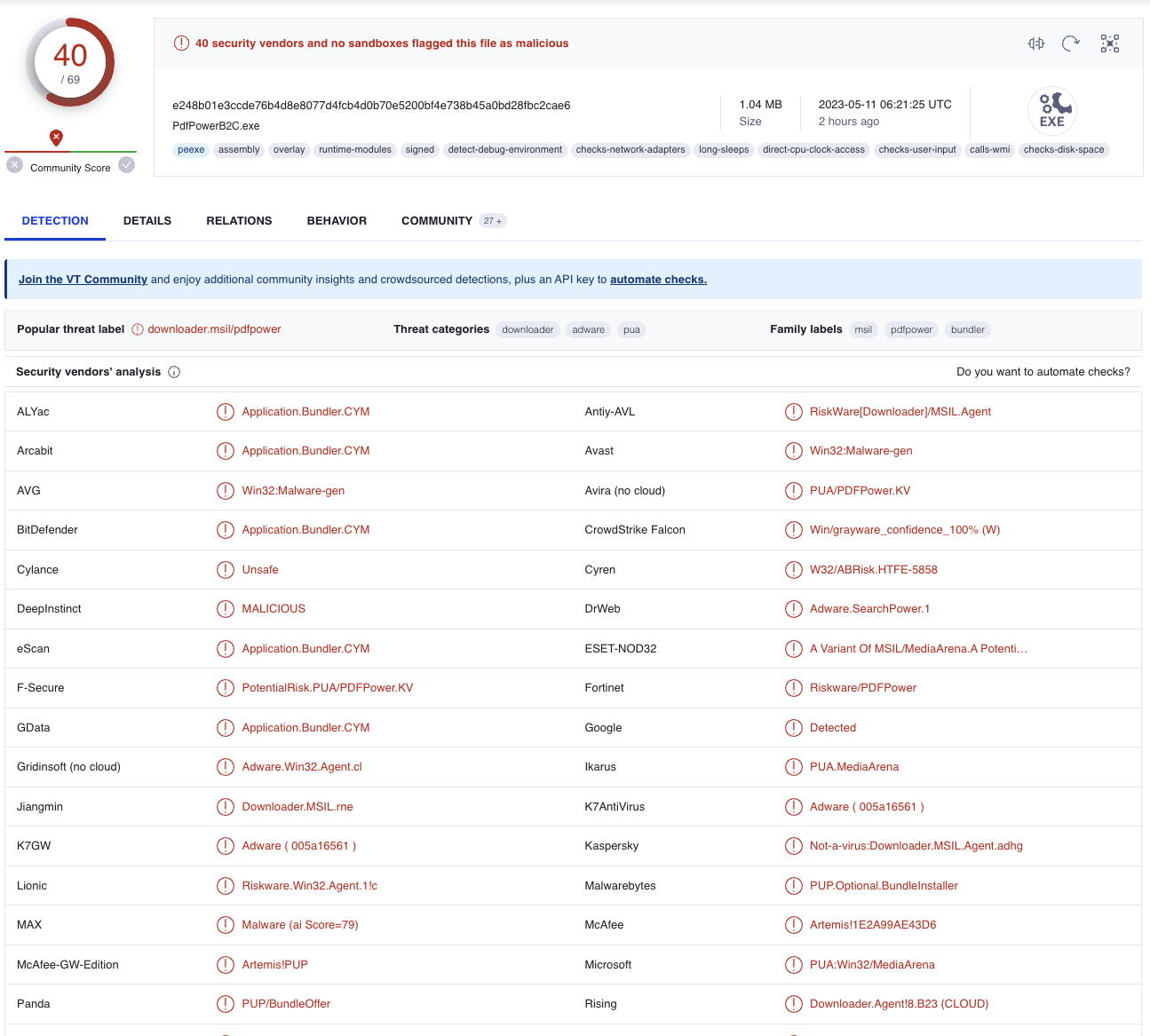
Detections for PUA happen quite a lot, and in most cases the effect of this type of program is benign. However, new detections of this same type kept coming in by the hour, which triggered us to dig deeper into the origin of the software.
The initial search, limited to a single customer of the Northwave SOC, already yielded more results for the file hash on multiple devices, with all of them being in the user’s Downloads folder. On some devices there were already multiple files by the same name (denoted by the ‘(#)’ in the file path, which is Windows default behaviour). A particular case showed that the file was downloaded more than 5 times.
Prevalence of the tool
Within the Microsoft platform, alerts related to this software had only come in over the past few days. To get a feeling for the prevalence of the tool, we decided to use the “Inventory” tool, available within Defender for Endpoint. Based on investigation on the type of software online, we found it had more than a single name. The list of all variants we found has been supplied below. In MDE, we saw that in the inventory, these variants all shared similar characteristics:
- The software name was always lowercase only.
- The software name and vendor were identical.
- The software version was always ‘1.0.0.0’.
Based on those characteristics, we queried the different environments:
DeviceTvmSoftwareInventory | where SoftwareName matches regex "[a-z]*" | where SoftwareVersion == "1.0.0.0" | where SoftwareName == SoftwareVendor
Obviously, post processing was needed to filter away benign software. Based on the known variants, we already had a prevalence of more than 600 hosts across more than 30 unique environments. A second observation was that most devices being affected by the software were using Microsoft Edge as their main browser.
Observed variants
- Gifsearchutils
- Gifsmakerpro
- PdfHub
- PdfMagic
- PdfMagicApp
- PdfPower
- PdfShark
- Screensearchutils
- Screensrecorder
- Searcharchiver
- Searchpoweronline
- Searchtoolshub
- Sharksearchonline
- Ziplikeapro
- Ziplikeaproapp
- Ziprararchiver
Browser Hijacking as main effect
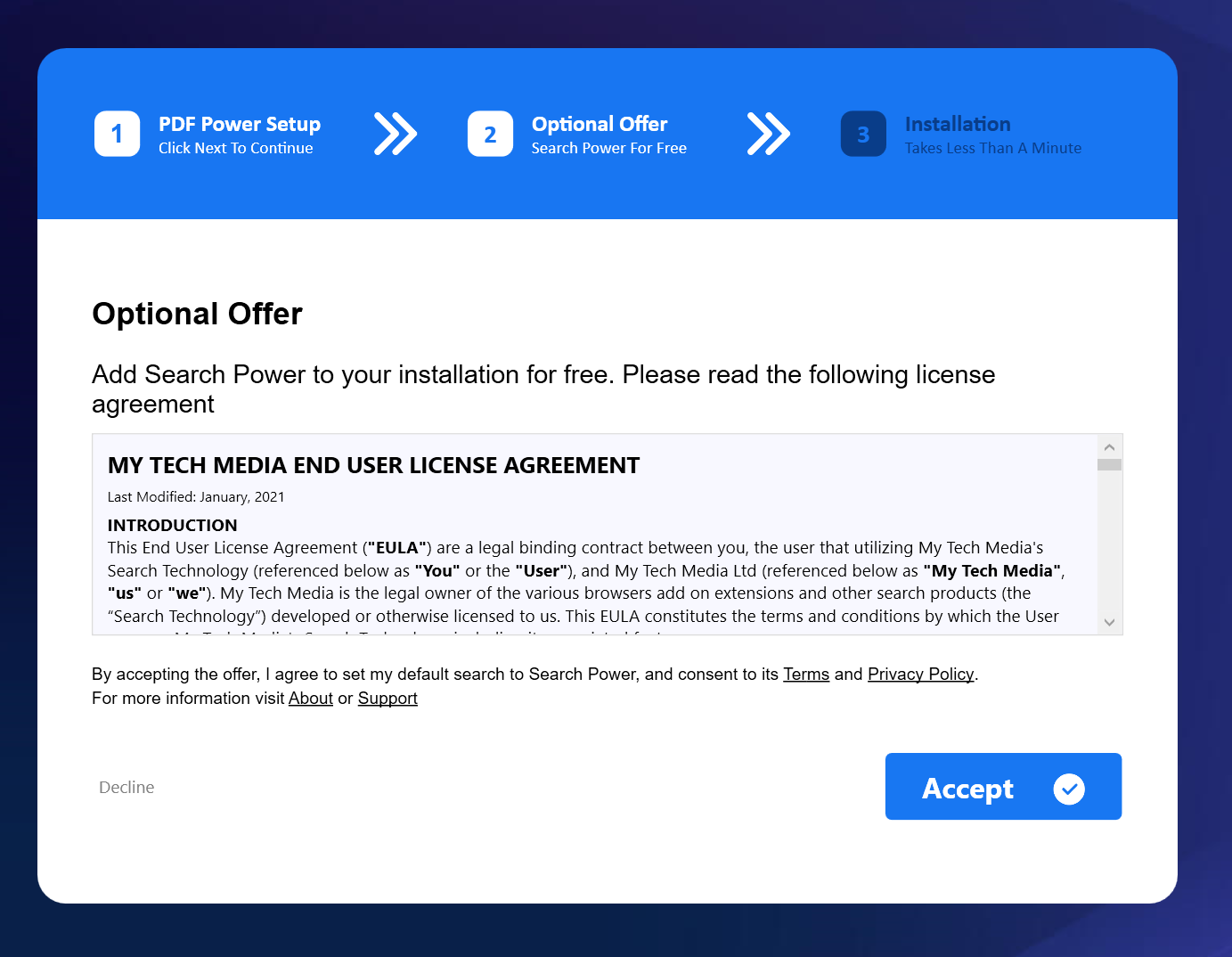
Upon running the program, an installer is presented. The theme and application to be installed depends on the particular strain. A commonly encountered strain is the PDF document converter. After confirming installation, the installer will display a progress bar. This progress bar is updated after randomized sleep, it does not track actual progress. In the background, the installer will tamper with the browser settings, by injecting key presses and directly injecting text into the clipboard. The browser settings are changed to use goto.searchpoweronline[.]com as the search engine. It will be listed in the search engines as AAsearchpoweronline.
Finally actual installation steps are taken:
- A shortcut is created on the users’ Desktop pointing to an online version of the tool it claims to install.
- A browser window is opened and directed to a thank you page for the installed tool.
- An uninstall option is created. Note that this uninstaller only removes the shortcut placed on the desktop. It does not restore the modified browser settings.
This behaviour is typical for a class of malware called “browser hijackers”. These programs try to overwrite certain settings in the browser to generate money, for example by injecting advertisements, or in this case, rerouting through a different search engine. Variants can steal data stored inside the user’s browser, like cookies or stored credentials. A likely source of monetisation is the data for searches performed by each unique user, which can be sold to third parties.
The observation of Microsoft Edge being the main browser of affected users was reinforced by opening the download link, which we found via the “Mark of the web” property of the file flagged by Microsoft Defender, in different browsers. Whenever the link was accessed using for example Google Chrome, the user would be redirected to the Google Store to install an extension.
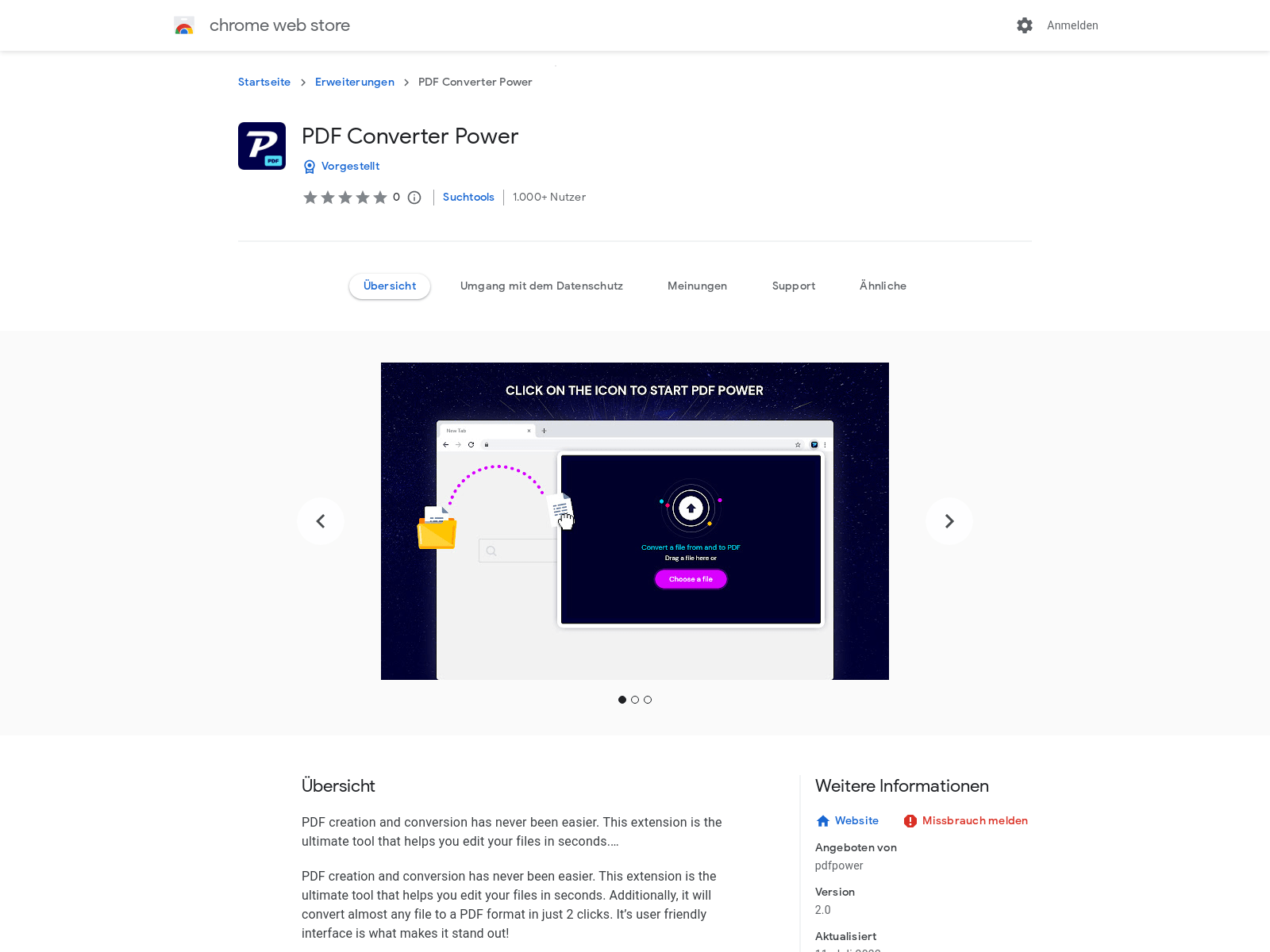
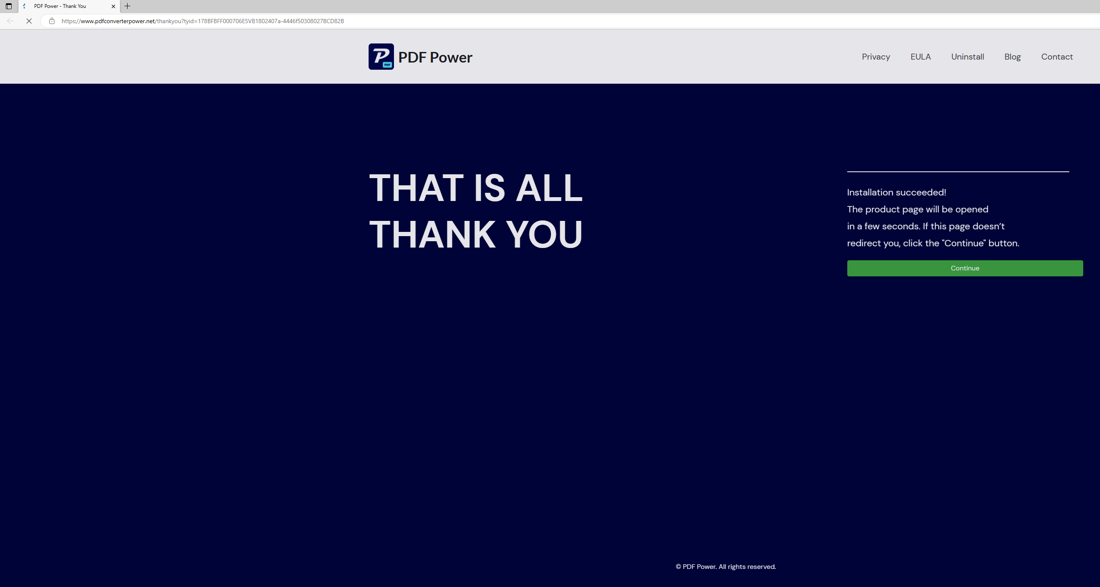
To find out how dangerous this browser hijacker is, we went into the technical details of the programs.
Technical investigation of MediaArena
Several samples of this adware strain have been analysed:
1. 5e1cec9e9011fc96638620a2ca8e08eeaeaea8a28c47fe619082abcc6794aebc
2. e9fad9727b8a66e6b593d8b416f1c60b692ffc91b72e14bb30c40a1ce9b6a260
E248b01e3ccde76b4d8e8077d4fcb4d0b70e5200bf4e738b45a0bd28fbc2cae6
All samples were PE files containing MSIL code. No obfuscation was used, but some fairly suspicious imports are done (VirtualProtect, SetWindowsHookEx).
The main class depends on the exact strain. In the analysed samples this was found to be either Struct or Infra. This class also carries the parameters for URL generation and campaign name:
- _strLogicSubdomain: prefix for search redirect
- _strReportSubmain: prefix for reporting
- AppId: some number likely identifying the application
- Identity: name of the strain
Browser setting modifications
To modify the browser settings, the installer injects key presses and changes the clipboard. Most of this functionality is found in the Simulation class. The class uses supporting functions from EchUtils to verify successful modification. While the installer is controlling the browser it also filters actual keypresses performed by the user. Only VK_RETURN, VK_TAB, VK_DOWN, VK_END, VK_T, VK_L, VK_CONTROL, VK_SHIFT are allowed. If a system is found to have multiple screens the installer will try the hijack. Presumably because the browser under installer control could be visible to the user.
Sending victim reports home
The installer sends back telemetry during the process. The telemetry is obfuscated before transmission using one of two xor keys and then base64 encoded. While the encoder contains two xor keys (anabel and takton), only takton is used for telemetry. All telemetry is made unique by concatenating some information about the system into a string. This string is stored in the main class in the suid member. This unique id consists of:
- CPUID
- Harddisk serial number
- MAC address for first interface
Telemetry is sent only during install. The following endpoints have been observed in samples:
- /find (not obfuscated)
- /v4/monetize (obfuscated)
- /upd (obfuscated)
- /report (obfuscated)
CPUID shellcode
The tools acquire the CPUID of the system by executing shellcode using VirtualProtect to allocate memory and CallWindowProcW to execute it. Functions are provided for both 32-bit and 64-bits x86 modes. Depending on IntPtr.size it picks one. Both functions simply invoke the CPUID instruction with EAX/RAX set to 1 (Processor info and feature bits) and return the outcome to the caller.
X86-64:
0000000000000000 53 PUSH RBX
0000000000000001 48C7C001000000 MOV RAX,00000001
0000000000000008 0FA2 CPUID
000000000000000A 418900 MOV DWORD PTR [R8],EAX
000000000000000D 41895004 MOV DWORD PTR [R8+04],EDX
0000000000000011 5B POP RBX
0000000000000012 C3 RET
X86-32:
0000000000000000 55 PUSH RBP
0000000000000001 89E5 MOV EBP,ESP
0000000000000003 57 PUSH RDI
0000000000000004 8B7D10 MOV EDI,DWORD PTR [RBP+10]
0000000000000007 6A01 PUSH 0000000000000001
0000000000000009 58 POP RAX
000000000000000A 53 PUSH RBX
000000000000000B 0FA2 CPUID
000000000000000D 8907 MOV DWORD PTR [RDI],EAX
000000000000000F 895704 MOV DWORD PTR [RDI+04],EDX
0000000000000012 5B POP RBX
0000000000000013 5F POP RDI
0000000000000014 89EC MOV ESP,EBP
0000000000000016 5D POP RBP
0000000000000017 C21000 RET 0010
Harddisk serial
There are three methods available for getting the harddisks’ serial number:
- WMI query SELECT * FROM Win32_PhysicalMedia
- WMI query SELECT * FROM Win32_DiskDrive
- Using ioctl’s to query SMART information
UUID
The UUID is generated using the UuidCreateSequential function in rpcrt4.dll.
Embedded DLLs
Various embedded DLLs were found. These are loaded at runtime by the EmbeddedAssembly class. The examined DLLs all turned out to be known and benign.
- PdfPower.Newtonsoft.Json.dll b624949df8b0e3a6153fdfb730a7c6f4990b6592ee0d922e1788433d276610f3
- PdfPower.WpfScreenHelper.dll cd2b9cf8489cca6b357bc2706a68f5a12aeb696380ce7371803d68f08e337630
- PDFSharkFF.LZ4.dll 6d37baeb841bcf6c4935a54f29df049d405df48345014cc12852b814d279d86e
How did so many devices get infected?
It is quite odd to have a tool that is suspicious being so widespread across different environments within a relatively short timeframe. Based on forensic evidence as well as talks with end users being affected, we found that the cause of at least part of the infections is an ongoing malvertising campaign. In which, advertisements are shown with content related to the current site. The user may be tricked into clicking the advert causing the tool to be downloaded.
E.g.: In a case we investigated, a user searched for a timetable of a ferry, got onto a legitimate website and then visited an advertisement URL, leading to the download of the malware. The user then executed this malware manually, presumably thinking it would provide information regarding the ferry.
MediaArena Removal process
The uninstall process only removed the shortcut from the desktop. This means that not all artefacts are removed. To completely clean up the program, several steps need to be taken, depending on the browser being used.
An extensive list of removal steps is provided by PCRisk [2]. In the case of Microsoft Edge, which is the most prevalent of browsers we have observed, the following actions need to be taken:
- Uninstall the program via the “Apps and Features” section in the Windows Settings.
- Remove the custom search engine from the settings in Edge:
- Open Microsoft Edge
- Select “Settings” (the three-dot icon next to the profile icon)
- Go to “Privacy and Services” and change the “Search engine used in the address bar” to a valid one (Bing, Google). If necessary, disable the unwanted search application.
- Select “Manage Search Engines” on the same page, and remove the installed one by the name starting with “AA”, e.g., “AAsearchpoweronline”
If the browser is not completely restored, you can always resort to “Reset Settings”, available in the Edge Settings menu. Your history and favourites will remain after using this option.
Preventing Unwanted Applications
This type of PUA is typically bundled with free software (freeware). During installation process of freeware, users may be presented with options to use a “quick” or “easy” installation. In the background, this will install secondary programs like the ones we have analysed here. As some of the tools supplied can also be used to upload documents like in the case of the PDF convertor, it may cause company data to end up at the creator of the tools. Therefore, preventing misuse of these tools is also a responsibility of the end user, who should think twice about uploading company data to an (unknown) web application. This can be facilitated in different ways:
- Users need to be aware of where to report suspicious or malicious behaviour, and they need to feel that it’s safe to report if they installed something they now have qualms about.
- Users need to be educated in the risks of installing software they find themselves on the internet.
- Users need to be aware of what tools they can use with company data.
Conclusion
In this post, we have shown the technical details of a newly detected PUA related to MediaArena. This variant is included in tools which claim to be PDF converters or other useful software. The software changes the search engine in the browser, allowing the attackers to harvest all search queries from users and serve them with tailored (potentially malicious) content. In the future tools like these could be expanded to perform more intrusive actions on a user’s PC. As this case proves again, be aware of any software you find on the internet, as it might not be what it tells you to be.
Sources
[1]: https://www.virustotal.com/gui/file/e248b01e3ccde76b4d8e8077d4fcb4d0b70e5200bf4e738b45a0bd28fbc2cae6
[2] https://www.pcrisk.com/removal-guides/25081-searchpoweronline-com-browser-hijacker