Is Your Ivanti Firewall Compromised?
How to Conduct A Forensic Investigation On Ivanti Devices

How to Conduct A Forensic Investigation On Ivanti Devices
Our Cyber Threat Intelligence team is closely following an increase in nation-state cyberattacks involving network edge devices. When Northwave’s cyber forensics experts investigated a vulnerability in the Ivanti Connect Secure (ICS), a next-generation firewall used by 35,000 customers worldwide, they uncovered how advanced threat actors can exploit it to gain access to internal systems, potentially leading to severe disruptions.
Last year, Northwave detailed how threat actors can compromise Ivanti’s legacy systems. Then, in early 2025, Ivanti disclosed a critical vulnerability known as CVE-2025-22457, revealing a buffer overflow issue that could lead to remote code execution. Despite initial claims that this was a low-priority error, Mandiant and Ivanti later found evidence of active exploitation dating back to mid-March. Investigators have linked China-nexus espionage actor UNC5221 to attacks that use this flaw to deploy sophisticated malware.
Keep reading for our technical analysis of how incident investigators can check for a system breach by performing forensic investigations on Ivanti devices.
Ivanti Compromises: Part Two
Performing digital forensics on Ivanti systems is challenging because disk encryption is employed to protect the contents of appliances and virtual machines from prying eyes. While in the past it was possible to use init=//bin/sh as a kernel boot parameter to skip init and go straight to sh, this has been disabled in more recent versions of the Ivanti software. Using this bypass allowed you to access the contents of the initrd image which contained the actual keys used for disk encryption. Given this no longer worked, Northwave investigators looked for a different way to get the key. As the initrd is somehow used by the kernel, the kernel needs to contain the keys and algorithms used to decrypt it.
By analysing the kernel used in the Ivanti software, we learned:
- A static AES key is used to decrypt the initrd
- The AES mode used is the same xor-encrypt-xor mode as used in legacy Ivanti, which we investigated in 2024.
- The static AES key differs between kernel versions
After extracting the key from the kernel, our expert was able to decrypt the initrd and get the LUKS key from /etc/lvmkey.
Extracting The Static Key
To decrypt the initrd image, code was added to the populate_rootfs kernel function. Unfortunately, symbols are stripped from the kernel and populate_rootfs is not part of the symbols exposed via /proc/ksymbols. One easy way to find this function is looking for a string starting with 07070100 which is used from the populate_rootfs function.
The added code uses cryptoapi to get an AES cipher instance, initialises it with the static key and decrypts the initrd image in memory. Decryption is done using the xor-encrypt-xor mode, as described in our first report on the vulnerability.
A different way to get this key has been implemented by the actors described in the CISA RESURGE report.
This leverages the fact that the key is constructed from 16 bytes in the .rodata segment of the kernel which are xorred with hardcoded constants to arrive at the AES key.
Initrd
The initrd contains a neatly documented /bin/init shell script:
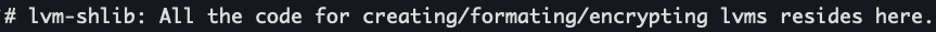
Continuing from /bin/lvm-shlib we found:
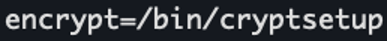
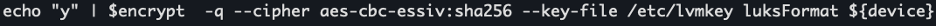
The contents of /etc/lvmkey also differs between software versions.
Next Steps For Ivanti Connect Secure Users
Organisations using the Ivanti Connect Secure firewall should immediately install the latest system update. Next, look for indicators of compromise, which is detailed in a table in the Mandiant report. If you do find evidence of a compromise or have questions, contact Northwave. Our NW-CERT team is available 24/7.
Even if you are not using this specific Ivanti product, all organisations should be aware of the heightened risks involving network edge devices. These systems–including firewalls, routers and VPN gateways–lack robust third-party protections, making them attractive targets for infiltration.
As our Cyber Threat Analysts also observed this year after exposing a stealthy breach of a Palo Alto Firewall system, even when these attacks are opportunistic, the methods used by threat actors are becoming increasingly complex and difficult to detect.
We are here for you
Need help with getting your organisation ready for DORA or wondering far along you your business currently is?
Get in touch and we will guide you with your next steps.
