Inside the world of ransomware dissecting the attack

Blog
Inside the world of ransomware, Part 1/3: dissecting the attack
Blog written by Noël Keijzer, Cyber security expert at the Northwave CERT
Northwave is a Dutch Cyber Security company currently located in the Netherlands, Germany, and Belgium, with ambitions to expand to other European countries in the future. The Northwave CERT responds to incidents all over Europe and has assisted companies in dealing with hundreds of ransomware attacks over the last years. From our experiences in dealing with these attacks we have formed a clear view on the realm of ransomware and the criminal ecosystem behind it. The number of ransomware attacks increases rapidly. In a likewise manner, the damage and political impact keeps growing at an alarming rate. To shed some light on this topic and to raise awareness for this issue, we will share our insights on the shadowy world or ransomware.
With this aim in mind, we will publish a three-part series of blog posts regarding ransomware. Part 1 of the series will provide the readers with insight into the activities that occur during a typical ransomware attack and introduce a framework for describing such an attack. Part 2 will focus on the different roles of the threat actors carrying out the attacks and it will introduce a model for describing the threat actors behind a ransomware attack. Finally, part 3 will elaborate on a ransomware affiliate that operated for several ransomware groups, showing that criminal collaborations are very fluid and constantly changing.
Introduction of the Unified Kill Chain
In this blog post, we dive into the world of ransomware attacks. The Northwave CERT handles dozens of ransomware attacks per year. Based on our investigations and experiences, we created a framework. This framework is derived from the Unified Kill Chain[1] and we believe it accurately describes the state of the current ransomware landscape. Through this blog post, we describe the key activities that we have seen during a ransomware attack. Next, we outline the objectives of these activities and show that they logically group into three different phases of an attack, that form the basis of the framework.
The framework
Paul Pols proposed the Unified Kill Chain in 2017 as a derivative of Lockheed Martin’s Cyber Kill Chain®[2], the MITRE ATT&CK framework[3] and a few other models. It divides cyberattacks into 18 unique activities—but not every activity occurs in every attack. The activities are divided into 3 phases, which we refer to in simplified terms as the IN, THROUGH and OUT phase. An overview of this framework can be seen in Figure 2. In the sections below we describe the key activities and the objectives we believe threat actors have within these phases.
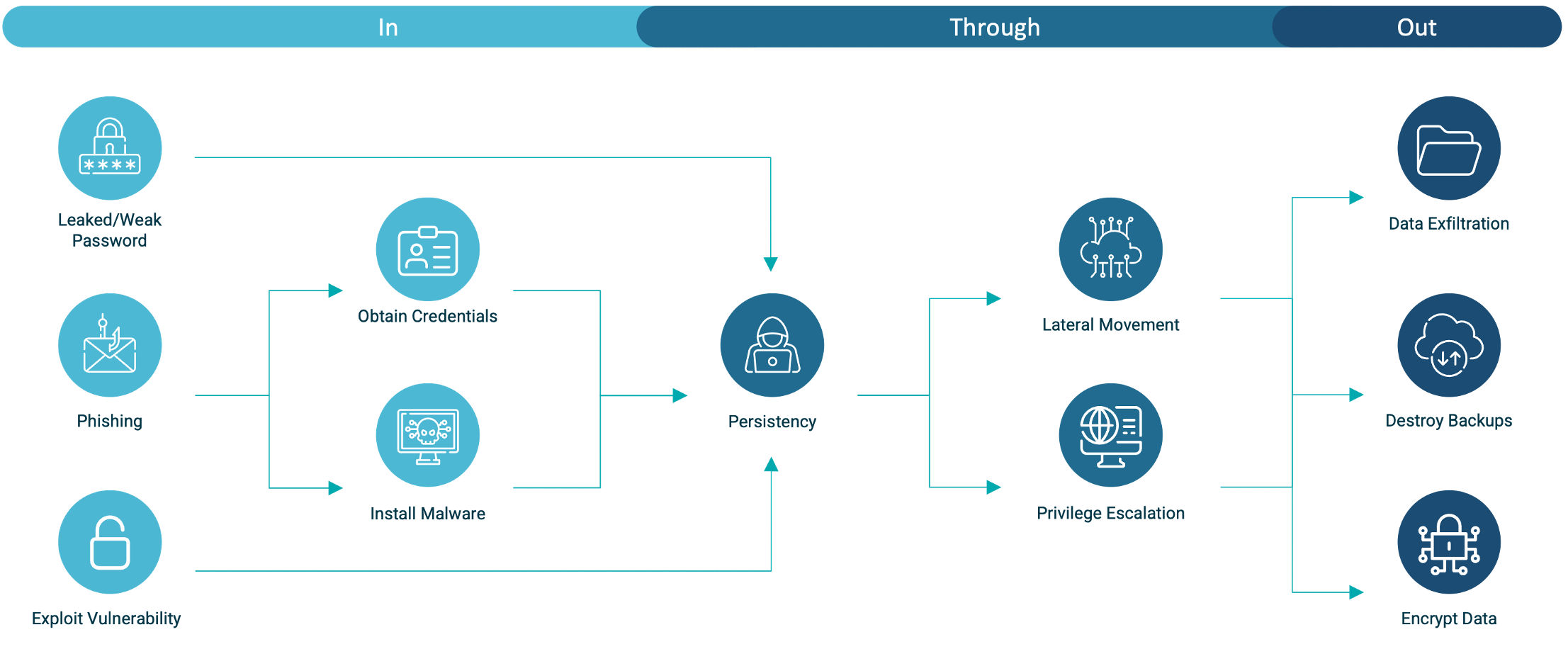
Figure 1: Phases of a ransomware attack
Key activities of a ransomware attack
The section below describes all the key activities that we identified with the Northwave CERT in typical ransomware attacks. We divided these activities into three different phases, based on the objective we believe the threat actors to have for each of them.
Obtaining initial access to the environment (IN)
In practice, we almost always encounter one of following three activities that threat actors use to gain initial access to an IT environment: (1) Abusing weak credentials, (2) exploiting vulnerable systems, or (3) phishing targeted at employees. Below, we explain these activities in detail.
- Abuse weak credentials
The first activity we frequently see during our CERT investigations is abuse of weak credentials. Threat actors frequently abuse weak credentials to gain access to networks. These actors often obtain network access by purchasing leaked credentials or brute-forcing of remote access solutions like VPNs or RDP services. Examples of leaked credentials are usernames and passwords present in data sets of VPN solutions, such as the recent leak of 500,000 Fortinet VPN credentials[4]. - Exploit vulnerability
The second activity that is frequently seen by the Northwave CERT, is the exploitation of recently released vulnerabilities to obtain access to a company’s networks. Threat actors will exploit such vulnerabilities on unpatched systems to gain a foothold in a network. Such exploits allow threat actors to install a backdoor on a system directly from the internet. Examples of this activity include the abuse of ProxyShell vulnerabilities[6], released in August 2021. - Phish employees
Finally, the third activity we often notice at the Northwave CERT that is related to obtaining access to environments is phishing. For this, threat actors utilise two different phishing techniques. The first technique often used by threat actors is credential phishing. It involves sending the target a seemingly legitimate e-mail that will trick them into filling in their credentials on a website crafted by the assailants to mimic a familiar website for the target. The second technique frequently used by criminals is phishing with malicious attachments. This technique involves tricking an employee into opening a document containing malware attached to a phishing e-mail[5]. When this malicious document is opened by the employee, a backdoor is installed on their system.
Figure 2: Example of a malicious phishing e-mail
Obtaining control of the network (THROUGH)
In almost every attack the Northwave CERT investigates, we observe activity to install persistency, move laterally within the network and obtain control over the network. Furthermore, we usually find that these three different activities occur parallel to each other. Below, we explain the various activities that take place during this phase.
Install persistency
In almost every attack, we see the threat actors installing a backdoor on the beachhead host. Subsequently, in most incidents, threat actors attempt to place additional backdoors on systems throughout the network, likely to ensure that they do not lose their grip on the environment when their victim discovers one of their backdoors.
Move laterally
Additionally, we always see that threat actors move laterally between systems and scan the victim’s network using network scanning software and tools to analyse the Active Directory. We believe that their objective for this activity is to obtain an overview of the network.
Escalate privileges
Finally, in all attacks, The Northwave CERT comes across activities related to privilege escalation. Usually, we find this activity in the form of execution of Mimikatz or through the exploitation of a vulnerable or incorrectly configured machine. We believe that the threat actors do this to obtain complete control of the environment by compromising an account with Domain Administrator privileges before moving to activity used to obtain leverage over their victim.
Obtaining leverage over the victim for extortion (OUT)
During most ransomware attacks, the last activities that the Northwave CERT detected includes the exfiltration of data, the destruction of backups, and the encryption of all data. All these activities are related to the ransomware attack’s final objective, to obtain leverage used to extort victims into paying a ransom.
Exfiltrate data
From experience, we gathered that most ransomware actors exfiltrate data as part of their modus operandi. They upload their victim's data to their servers or, on certain occasions, to cloud storage products such as Mega or Google Drive. By threatening victims to publish the exfiltrated data, these actors put additional pressure on the victim during negotiations. If sensitive data becomes available for download, this could harm companies, reveal intellectual property, or even lead to legal or contractual fines.
Destroy backups
In all attacks that we investigate, we find that the threat actors attempt to destroy all available backups. This step is crucial and necessary before encrypting the company's data. Otherwise, a company would revert their data to a version from a backup, which would provide an option to restore their systems without paying the ransom. Hence, the actors' objective is to leave a victim with no other choice than to pay the demanded ransom.
Encrypt data
Finally, each ransomware attack ends with the encryption of data of the victim company. Threat actors aim to encrypt all data to halt business operations, which results in a situation where the victim can either pay for the decryption of their data or lose all their data and face losses far more significant than the demanded ransom.
Conclusion
The Northwave CERT has shown that the key activities of a ransomware attack naturally fall into three different phases, based on their objective. More specifically, obtaining initial access to the environment, obtaining control of the network, and obtaining leverage over the victim for extortion. Based on that, we developed a framework derived from the Unified Kill Chain that describes attacks as consisting of three different phases, containing activities that revolve around achieving the aforementioned objectives.
Mitigations
There are several mitigations that companies can take to reduce the risk of suffering a ransomware attack. In our experience, there are a few key mitigations that companies can take to lower the risk of a ransomware attack significantly.
Multi-Factor Authentication
In various ransomware cases we investigated, the victim could have avoided the attack if they had enforced Multi-Factor Authentication (MFA) for all users. Such a measure would substantially reduce the chance that attackers gain access to a company network by abusing weak or phished credentials.
Patch management
Furthermore, we noticed threat actors abused unpatched or outdated operating systems in several cases we investigated. Either to gain initial access to the environment or to elevate privileges during the attack. Proper patch management could prevent attackers from gaining access to systems or administrative credentials.
Backup policy
Additionally, with a decent backup policy implemented, you can significantly lower the impact of ransomware attacks. A proper backup policy will ensure that even if a ransomware attack occurs, intruders cannot destroy all backups and that you can restore their environment without fulfilling the demanded ransom.
Security Monitoring
Finally, a security monitoring solution that monitors all systems on the network will significantly lower the chances of suffering from a ransomware attack. A proper security monitoring solution will alert you of any malicious attempts to gain access to your network, as well as any malicious activity occurring within the network. Allowing you to immediately act on such threats, before ransomware can be deployed throughout your network.
Stay tuned for part 2 of this series! In the second blog post, we will dive into the criminal world behind a ransomware attack. We will describe the roles in a ransomware kill chain based on open-source intelligence and our own experiences in dealing with threat actors.
Sources:
- [1] https://www.unifiedkillchain.com/assets/The-Unified-Kill-Chain.pdf
- [2] https://www.lockheedmartin.com/en-us/capabilities/cyber/cyber-kill-chain.html
- [3] https://attack.mitre.org/
- [4] https://www.bleepingcomputer.com/news/security/hackers-leak-passwords-for-500-000-fortinet-vpn-accounts/
- [5] https://northwave-security.com/en/qbot-spam-campaign/
- [6] https://techcommunity.microsoft.com/t5/exchange-team-blog/proxyshell-vulnerabilities-and-your-exchange-server/ba-p/2684705
