Why Supply Chains And Edge Devices Are The Next Cyber Security Battleground For Businesses

Is a ticking time bomb hidden in your supply chain or firewall system?
Publication date: December 19, 2024
Northwave’s latest cyber threat intelligence shows that these interconnected systems are increasingly exploited by nation-state actors and advanced cybercriminal groups.
The reason is simple: supply chains often house the weak links in an organisation’s defences, while network edge devices–such as firewalls, routers and VPN gateways–lack robust third-party protections, making them attractive targets for infiltration. That said, even when these attacks are opportunistic, their methods are becoming increasingly complex and difficult to detect.
We encountered a prime example of this development during a recent incident response involving one of our clients, a multinational company. At first glance, the compromise appeared to be the result of a basic and commonly used infiltration strategy. However, after a more in-depth investigation, Northwave’s Computer Emergency Response Team (CERT) team uncovered a sophisticated, customised attack technique that pointed to a much more highly skilled threat actor than originally suspected.
While the tailored tactic was unique, we see this incident is a harbinger of the challenges organisations face in assessing risks in their third-party suppliers and edge devices. Nation-state attackers from countries such as China and Russia are putting smaller companies, including IT suppliers, and vulnerable edge devices in their crosshairs as they seek to infiltrate more well-defended networks. Meanwhile, ransomware criminals are weaponizing supply chain dependencies to breach multiple organisations at once.
Here's a closer look at how this particular firewall infiltration unfolded and what businesses can do to fortify their cyber defences as the attack surface expands.
From Vulnerability Disclosure to Advanced Attack
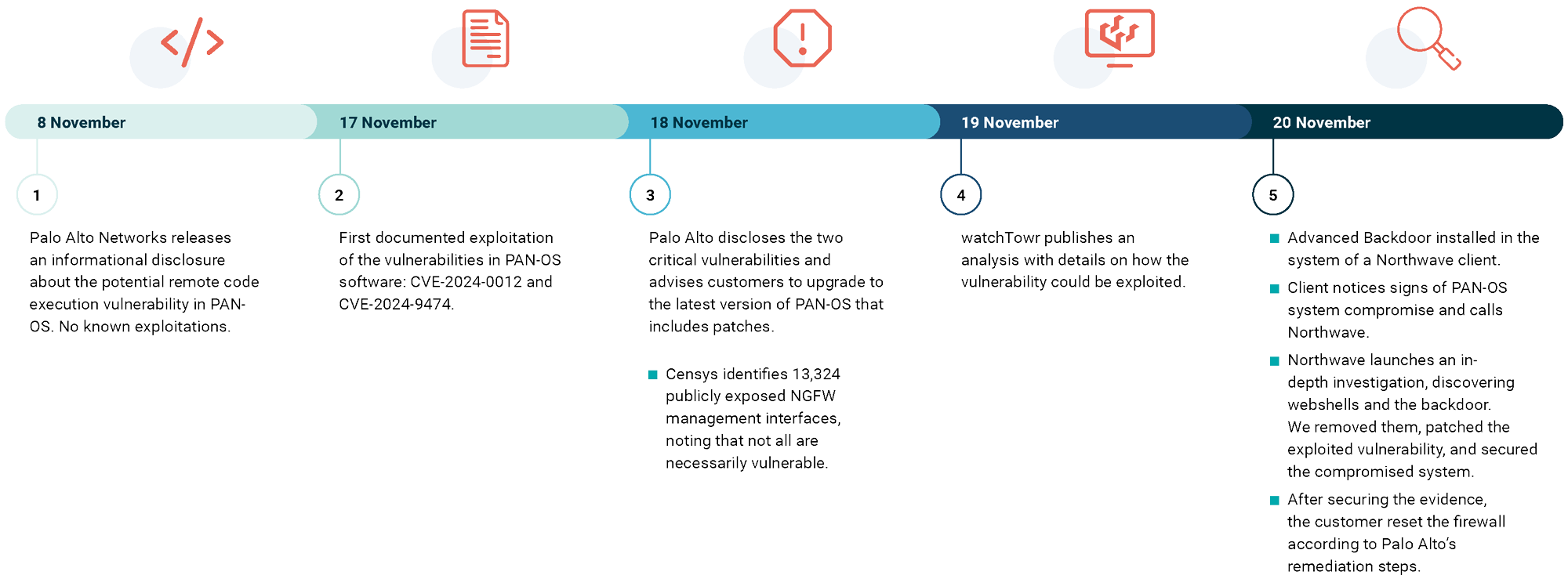
On 8 November 2024, Palo Alto Networks disclosed a critical vulnerability in their firewall systems, urging users to patch their edge devices immediately. Initially categorised as a standard risk, the vulnerability’s severity was elevated less than two weeks later. The following day, the cyber security publication watchTowr released a detailed analysis, reverse-engineering the vulnerability and publishing technical insights.
While the article provided valuable information for defenders, it also provided a blueprint to abuse unpatched systems. Exploitation began almost immediately, with malicious actors deploying web shells to compromised systems. These tools allowed remote access and control, enabling attackers to maintain a foothold in the affected networks.
Soon after watchTowr published the proof-of-concept exploit, we received a call from a Northwave client after they noticed unusual activity in their firewall logs that included suspicious commands and other signs of abuse. Our CERT team began analysing diagnostic packages provided by the firewall. This included configuration files and logs that showed exploitation attempts. We found that, at some point, attackers took advantage of the known vulnerability in our client’s Palo Alto firewall that allowed unauthorised access into the system.
As described in the watchTowr report, we found evidence of a web shell, which are malicious scripts uploaded to servers, opening the door to remote access and control. Although unsophisticated, they are often deployed for persistence and lateral movement within compromised systems.
Due to our ongoing research into evolving global threat landscape, we know that nation state actors and advanced ransomware groups are intensifying their focus on network edge devices. Therefore, our experts didn’t stop at standard tools and investigative methods that could miss more sophisticated threats. The team kept digging with a full forensic analysis, making a complete copy of the compromised system’s filesystem.
This deeper investigation, aided by insights from the watchTowr report, revealed a hidden backdoor—a tool an attacker, likely a nation state actor, specifically adapted to exploit the known vulnerabilities in Palo Alto’s systems. Due to the clear difference in the skill levels required for each of the attacks, we suspect they are the work of separate threat actors. The investigation is still ongoing as to the originating nation of the nation state actor group behind the tailored backdoor.
Notably, the backdoor operated at a lower system level, making it invisible to standard monitoring tools and undetectable through basic diagnostic checks. It also had persistence mechanisms that allowed it to maintain access even after basic mitigation steps. The threat actors’ high level of skill and planning meant that our proactive approach and forensic expertise were crucial in exposing this attack.
Learn more about the technical specifications of this incident in Northwave’s in-depth reverse engineering analysis.
Palo Alto Edge Device Attacks
The following PAN-OS versions are vulnerable:
o PAN-OS 11.2 versions < 11.2.4-h1
o PAN-OS 11.1 versions < 11.1.5-h1
o PAN-OS 11.0 versions < 11.0.6-h1
o PAN-OS 10.2 versions < 10.2.12-h2
o PAN-OS 10.1 versions up to 10.1.14-h6
The vulnerabilities affect PA-Series, VM-Series, and CN-Series firewalls, as well as Panorama (virtual and M-Series) and WildFire appliances.
CVE-2024-0012 is an authentication bypass vulnerability (status: critical) that allows unauthenticated attackers to gain administrative privileges on affected PAN-OS devices. The vulnerability exists in the uiEnvSetup.php script and can be exploited by crafting a malicious HTTP GET request with the X-PAN-AUTHCHECK header set to "off".
CVE-2024-9474 is a privilege escalation vulnerability (status: medium) that enables authenticated attackers to execute commands on the firewall with root privileges. The vulnerability is found in the createRemoteAppwebSession.php script.
When chained together, these vulnerabilities allow unauthenticated remote code execution (RCE) on the PAN-OS management interface. Palo Alto Networks recommends upgrading to the latest version of PAN-OS that includes patches for these vulnerabilities. Organisations should secure access to the management interface by restricting access only to trusted IP addresses.
Ticking Time Bomb in the Supply Chain
The precision and persistence of this backdoor exemplifies how even opportunistic attackers are leveling up their methods to outpace standard defences. Although the attackers’ full motives remain unclear, potential risks range from nation state-sponsored espionage to broader supply chain attacks. These ad-hoc, yet skilful, attacks highlight a trend that we’ve been watching closely in our threat landscape research. Since cybercriminals often target publicly known vulnerabilities, unpatched systems can become latent threats in the supply chain.
The risks for companies of all sizes and across different sectors are significant. For example, smaller organisations may become collateral damage, or used as stepping stoneshen tools or techniques developed for targeting specific entities are widely exploited after becoming public knowledge. In the case of our client, even if the business wasn’t specifically targeted, the backdoor posed a serious risk. If it had gone unnoticed, the threat actor could have returned later to further explore the network or might already have been doing so.
A common misconception is that opportunistically exploited organisations aren’t high-value targets for the attacker. On the contrary, the company might offer economic insights, act as a supplier in a broader supply chain, or have strategic significance. Even if the attackers themselves don’t act on this access, they could sell it to other malicious actors. This latest incident is a good example of how advanced techniques, initially used for targeted attacks, are increasingly repurposed for financial gain and broader exploitation.
“The attack surface is expanding. Attackers are becoming more 'holistic' in their approach, covering an organisation’s entire ecosystem. While organisations are facing greater dependencies on third parties, threat actors are bypassing defences by making clever use of weaker links within supply chains, especially through IT and software suppliers. Attacks are more frequently cloud-based, as enterprises are moving their IT to the cloud. Vulnerabilities in edge devices are exploited in an instant.” Northwave 2024 Global Threat Landscape
Here are some key developments we see in threats to the supply chain:
- No Organisation Is Too Small: With supply chain interdependencies, even smaller companies are targets. Attackers exploit these connections, making vigilance essential through the entire chain.
- Opportunistic Attacks Are Trending: Threat actors often target publicly known vulnerabilities, meaning unpatched systems are prime targets.
- Urgency is Imperative: Complacency is no longer an option. All organisations must act swiftly to address vulnerabilities and implement proactive defence strategies.
- Collateral Damage Is Real: Businesses not directly targeted may still be affected, either as entry points for attackers or as unintended victims. Our client lost one day of business operations during the investigative process but the full impact of the incident on their global operations is still not clear.
The interconnected nature of today’s digital landscape means we’re all part of a broader security ecosystem. As such, your cyber security extends well into your third-party IT suppliers. Organisations must act not only to protect themselves but also to safeguard their partners, customers, and ultimately their brand reputation.
Our Expert Recommendations
As supply chains and network edge devices increasingly become targets for advanced threat actors, businesses must recognise the vulnerabilities these systems present. We recommend taking these steps:
- Swiftly and thoroughly evaluate vulnerabilities: Conduct immediate checks for all known vulnerabilities, especially those exploited in recent attacks.
- Thoroughly Assess Supply Chain Risks: Identify all risks in your supply chain, even down to the software that runs on your servers and workstations–including network edge devices.
- Strengthen Patch Management: Treat patching as a priority, not an afterthought, to reduce exposure windows. Given the extremely high frequency of urgent vulnerability reports, this will require developing a strong risk management approach.
- Partner with Experts: Quickly engage cyber security specialists to proactively monitor and defend against threats.
At Northwave, we don’t just react to attacks; we predict and prevent them so our clients can stay ahead of evolving threats. With our expertise in forensic investigation, reverse engineering, and global threat analysis, we help organisations turn potential disasters into resilience.
Don’t wait for the next attack. Contact Northwave today to safeguard your business assets.
We are here for you
