Vulnerability Notice Topaz Antifraud
CVE NUMBER
CVE-2023-52271
CVSS SCORE
6.8 - CVSS:4.0/AV:L/AC:L/AT:N/PR:L/UI:N/VC:N/VI:N/VA:H/SC:N/SI:N/SA:N
SUMMARY
During recent kernel driver research, we identified a vulnerability in Topaz Antifraud, a software solution used by Brazilian and Spanish banks, to combat bank fraud. The vulnerability can be utilised to make a new implementation of Blackout; a tool to kill anti-malware protected processes.
Impacted Versions
At least the following version is affected (and likely also lower versions).
- Topaz Antifraud wsftprm.sys 2.0.0.0
DETAILS
The vulnerable driver creates a driver device which can be accessed by any user on the system. The driver device supports an IOCTL handler that allows any user to make abitrary calls to kernel functions that aid in killing any process on the target system. More details will be published in a blog post once the vulnerability has been patched by the vendor.
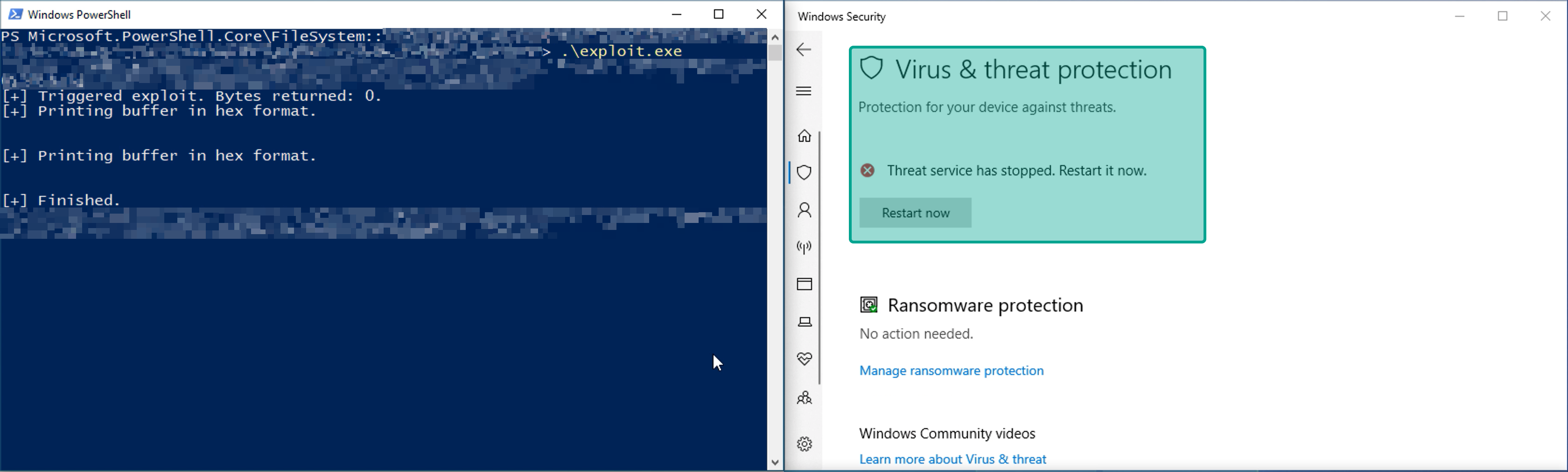
Northwave’s reverse engineering team was able to build a fully functional exploit that allows any user on the system to kill Protected Process Light (PPL) processes, such as Microsoft Defender.
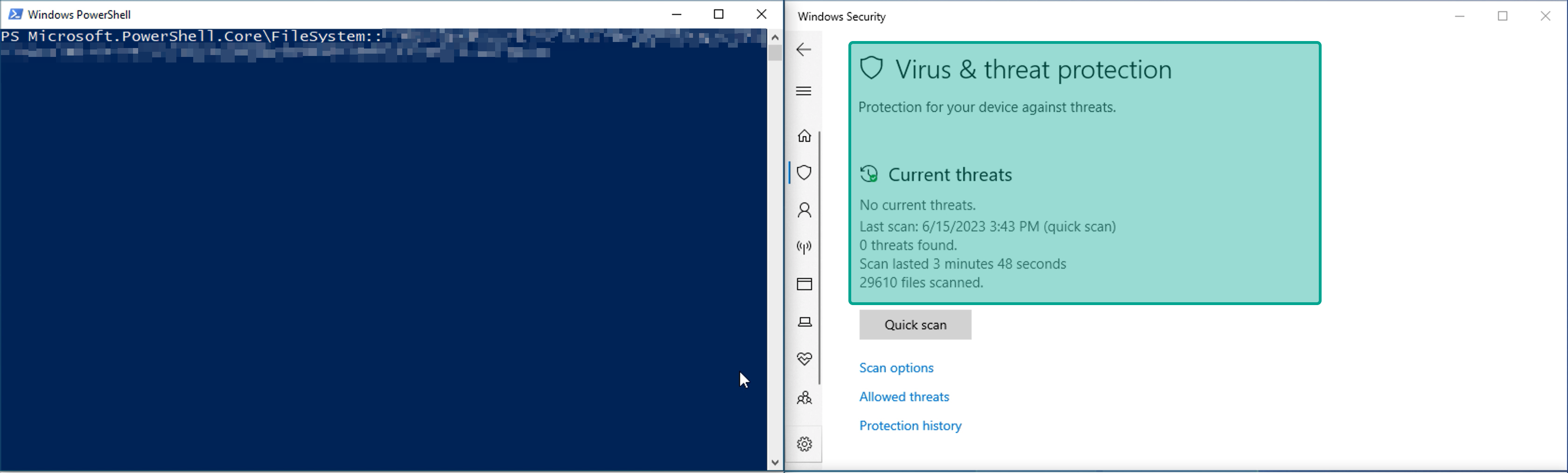
Microsoft Defender running before execution of exploit:
Microsoft Defender stopped working after execution of exploit:
TIMELINE
- 11-09-2023 - Initial notice to Topaz and request for security contact.
- 12-09-2023 - First reply from Topaz requesting more information.
- 13-09-2023 - Sent full vulnerability details to Topaz.
- 18-09-2023 - Topaz notified Northwave of vulnerability triage.
- 10-10-2023 - Topaz notified Northwave of remediation planning.
- 10-10-2023 - Topaz released a patch for the vulnerability.
- 01-01-2024 - Mitre assigned CVE-2023-52271.
- 10-02-2023 - Planned public release.
REFERENCE
Topaz Antifraud: https://www.topazevolution.com/en/antifraud/
CREDIT
Discovered by Tijme Gommers, Jan-Jaap Korpershoek and Alex Oudenaarden of Northwave Cyber Security
Disclaimer
Northwave has made every effort to make this information accurate and reliable. However, the information provided is without warranty of any kind and its use is at the sole risk of the user. Northwave does not accept any responsibility or liability for the accuracy, content, completeness, legality or reliability of the information provided. We shall not be liable for any loss or damage of whatever nature, direct or indirect, consequential or other, whether arising in contract, tort or otherwise, which may arise as a result of your use of, or inability to use, this information or any additional information provided by us in direct or indirect relation to the information provided here.
